Configuring the Default Internal Network on the Edge ISA Firewall
When the edge ISA firewall was installed, it took its definition of the default internal network from the routing table on the edge ISA firewall device.The routing table entries indicated to the ISA firewall installer that the addresses 10.0.1.0 through 10.0.1.255 should be included in the definition of its default internal network.This is a correct configuration if the only network behind the edge ISA firewall was on network ID 10.0.1.0/24. However, in our scenario, this is an incorrect configuration and will cause problems with access controls on connections to and from the network services segment through the edge ISA firewall.
| Note | If the ISA firewall device’s routing table had been configured with a routing table entry for the network services segment located behind the network services segment perimeter firewall, the ISA firewall software’s installer program would have seen this routing table entry and included that network ID as part of the edge ISA firewall’s definition of its default internal network. |
The reason for the problem with the initial settings for the default internal network on edge ISA firewall is that there is a Route relationship between the Corpnet ISA firewall network (which is the edge ISA firewall’s default internal network) and the default internal network behind the network services segment ISA firewall. Because there is a Route relationship, connections from SecureNAT clients located behind the network services perimeter ISA firewall will reach the edge ISA firewall with their original client IP address included as the source address (note that this is not the case with proxied connections by Winsock [Firewall] and Web proxy clients). If we leave the edge ISA firewall’s default internal network definition as it is now, connections from SecureNAT clients located behind the network services perimeter ISA firewall will be detected as spoofed packets.
ISA firewall networks are used to determine the validity of connections reaching the interface that is the “root” of a particular ISA firewall network. For the edge ISA firewall, the root of its default internal network is the internal interface which is on network ID 10.0.1.0/24. Any connections with a source IP address on that network ID are seen as valid. That is to say, they are seen as not being spoofed.
However, if a connection with a source IP address that is not part of the edge ISA firewall’s default internal network’s definition is made through the interface that is the root of the edge ISA firewall’s default internal network (which is the internal interface of the edge ISA firewall), the connection is dropped as a spoof attempt.The ISA firewall assumes that it’s not possible for an interface to accept a connection from a host on an ISA firewall network that isn’t the same as that for which the interface is root.
We can easily solve this problem by adding the IP addresses included in the network services perimeter ISA firewall’s default internal network (which is the network services segment) to the definition of the edge ISA firewall’s default internal network definition.
Adding IP Addresses of the Network Services Perimeter Segment to the Front-End ISA Firewall’s Default Internal Network
Perform the following steps to add the IP addresses of the network services perimeter ISA firewall’s default internal network to the definition of the front-end ISA firewall’s default internal network:
-
In the ISA firewall console, expand the server name and then expand the Configuration node. Click on the Networks node.
-
On the Networks node, click the Networks tab in the Details pane, then double click the Internal network.
-
In the Internal Properties dialog box, click the Addresses tab.
-
On the Addresses tab, click the Add button.
-
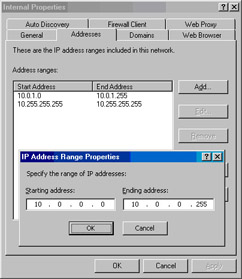
In the IP Address Range Properties dialog box, enter the Starting address and the Ending address in the text boxes. In this example, we’ll enter 10.0.0.0 and 10.0.0.255, respectively. Click OK (see Figure 10.35).
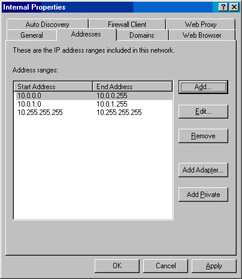
Click OK in the Internal Properties dialog box (see Figure 10.36).
IP addressing information for hosts on the Corpnet network is determined by your requirements.The most secure configuration is to not provide users with a default gateway address that provides a route to the Internet.This forces all users to use the Firewall client and Web proxy configuration, which can be used to enforce strong user/group-based access controls, as well as block applications installed on users’ computers from accessing the Internet.This also prevents users from using non-Winsock or Web proxy-compliant applications, such as Internet Control Message Protocol (ICMP) utilities such as PING and TRACERT.
Administrative users and servers can be configured with gateway addresses that route to the Internet. Administrators require the use of ICMP-based utilities, and servers do not have logged-on users, so both admins and servers require the facilities provided by the SecureNAT client configuration.
I should note that this can be problematic for networks that have LAN routers, as you must configure the clients to use the LAN routers as their default gateways. However, if you are using the ISA firewall as your edge firewall, this will not be a problem, as you can allow only administrative users access to non-Winsock protocols, such as ICMP and virtual private network (VPN) protocols.
Creating a Routing Table Entry on the Edge ISA Firewall
A routing table entry must be configured on the edge ISA firewall so that it knows the path to take to reach the network services segment.The ISA firewall should always be configured with routing table entries for all network IDs that can’t be reached using the default gateway. In practice, this usually means that except for Internet addresses, there should be a routing table entry on the ISA firewall for all network IDs on your corporate network.
Note that if your ISA firewall is configured with a default gateway pointing to a LAN router, and all network IDs are reachable from that router, there’s no reason to enter all network IDs in the ISA firewall’s routing table, because the LAN router is performing the router duties.
At the edge ISA firewall, open a command prompt and enter the following:
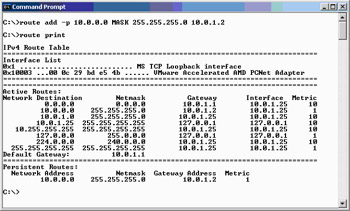
route add –p 10.0.0.0 MASK 255.255.255.0 10.0.1.2 In the preceding code, 10.0.0.0 is the network ID for the network services segment behind the network services perimeter ISA firewall, 255.255.255.0 is the subnet mask for that network ID, and 10.0.1.2 is the IP address on the external interface of the back-end ISA firewall.
Figure 10.37 shows an example of configuring the routing table entry.
Joining the Edge ISA Firewall to the Domain
The edge ISA firewall should be a member of the domain so that you can fully leverage both the firewall and the Web proxy client configuration. Although you can use RADIUS authentication for Web proxy clients, there are significant limitations to RADIUS authentication in both the logging and the management realms. For this reason, I recommend that you avoid RADIUS authentication if at all possible. In addition, you must make the edge ISA firewall a domain member if you want to fully leverage the enhanced security and flexibility provided by the Firewall client.
The edge ISA firewall will be able to use the intradomain communications Access Rule created on the network services perimeter ISA firewall to access the domain controller.The edge ISA firewall is configured to use the DNS server on the network services segment, which is configured to support name resolution within the network and for Internet host names.
I should note that making the edge ISA firewall a domain member is specific for this scenario only, where the clients are located directly behind the edge ISA firewall. If you encounter resistance to joining the edge ISA firewall to the domain, you can easily place another ISA firewall in front of the edge ISA firewall in this scenario and then create rules that allow the required inbound and outbound connections, only not requiring any type of authentication. In this type of deployment, the ISA firewall would be acting in the same way as a typical “hardware” firewall.




0 comments
Post a Comment