What is Directory Service?
A Directory Service is a software application that stores and organizes information about the network users and resources. The Directory Service
allows the network administrators to manage the user’s access to the
resources. The Directory acts as a central point of control and
management of the network operating system.
Main advantages of Directory Services are
Directory Services help in Simplifying management: By acting as a single point of management, a directory can ease the administrative tasks associated with complex networks.
Directory Services provide higher level of security. Directories offer a single logon facility and they provide more secure authentication process.
Directory Services allow interoperability: Most of Directory Services
available today are based upon industry standards like X.500,
Lightweight Directory Access Protocol (LDAP) etc. This allows sharing of
resources in a heterogeneous environment.
Directory Services software application store data in its own database. Following are the important data which are kept in Directory Services database.
• User Account Information (Login name, Password, Restrictions).
• User Personal Information (Phone number, Address, Employee ID).
• Peripheral Configuration Information (Printers, Modem, Fax).
• Application Configuration (Desktop Preference, Default Directories).
• Security Information.
• Network Structure.
• Network Infrastructure Configuration.
Introduction to Directory Standards
International Telecommunication Union (ITU) and International Organization of Standardization (ISO) proposed X.500 standard in 1988.
X.500 was a very
good Directory Standard and provided a lot of new functionality and
security. The problem with X.500 was it was difficult to implement. The
X.500 Directory Access Protocol (DAP) was too complex and was using OSI
network protocol instead of TCP/IP.
Lightweight
Directory Access Protocol (LDAP) was developed after X.500 and LDAP was
based on X.500. Since
Lightweight Directory Access Protocol (LDAP) was
originated from X.500, the structure of X.500 and Lightweight Directory
Access Protocol (LDAP) directories are almost similar. LDAP directory
implementations are often also X.500 compliant.
The first version
of the Lightweight Directory Access Protocol (LDAP) was released in 1993
as RFC 1487 and it was not successful because of the absence of many features provided by X.500. The University of Michigan scientists released the first LDAP directory server, as RFC 1777 (LDAPV2) in 1995 and it became the basis for many future directory servers.
LDAP version 3 (v3) is defined by nine RFC documents. RFC’s 2251
through 2256 give the core details, and were later followed by RFC 2829,
2830 and 3377. All these RFC’s together known as LDAPV3. LDAPV3 was
released on December 1997.
What is Active Directory® (AD)?
Active Directory® is the Microsoft's implementation of Directory Services its purpose is to store information about users, resources, and other network components, and to provide that information according to access permissions of the entity who is requesting it.
Active Directory (AD) is meant for use in Microsoft Windows network environments and it provides central authentication and authorization services for Windows-based computers.
Active Directory uses Lightweight Directory Access Protocol (LDAP), which is derived from X.500 data model. Hence Active Directory is X.500 compliant.
The Directory
Service should provide an efficient way to manage, find and access all
the resources (computers, users, printers etc) in the network. The
following are the features which should be provided by a good Directory
Service implementation. Microsoft’s Directory implementation (Active Directory®) addresses all these issues.
Centralization: Active Directory is centralized directory implementation providing a single database of network resources.
Scalability: Active Directory allows its database to be partitioned and distributed across the domains that make the network. But still Active Directory can be managed as a single directory.
Standardization: Active Directory is standardized because it is made accessible through Lightweight Directory Access Protocol (LDAP), which is an IETF standard.
Extensible: Active Directory is extensible. It allows third-party developers to store the information of their own application inside Active Directory and make use of the features provided by the Active Directory.
Separation of physical network: Active Directory makes the physical structure of the network transparent and only the local structure is visible to the users.
Security: Active Directory is tightly integrated with the Windows 2003 server security and the major security protocols make it more secure.
Domain Name System (DNS) support: The Active Directory supports Domain Name System (DNS) and Active Directory requires DNS to function properly.
TCP/IP compatibility: Active Directory and Windows Server 2003 utilize the TCP/IP protocol stack as their primary method of communications.What is an Active Directory (AD) Forest?
An Active Directory forest is the largest logical container (An Active Directory container is also an Active Directory object that holds other Active Directory objects. Other Examples of Active Directory Container objects are Active Directory Domains and Organizational Units (OUs)) within Active Directory which holds all Active Directory domains together. All domains in an Active Directory forest are linked together via transitive trusts that are created automatically.
The main characteristics of an Active Directory forest are:
• All domains within a forest share implicit two-way transitive trusts with the other domains within the forest.
• All domains within an Active Directory forest share a common Active Directory schema.
• Noncontiguous namespace and differing name structure.
• All domains share a common global catalog.
• Active Directory domains are independent. Cross-domain communication is enabled by the Active Directory forest.
A typical structure of an Active Directory forest is shown below.
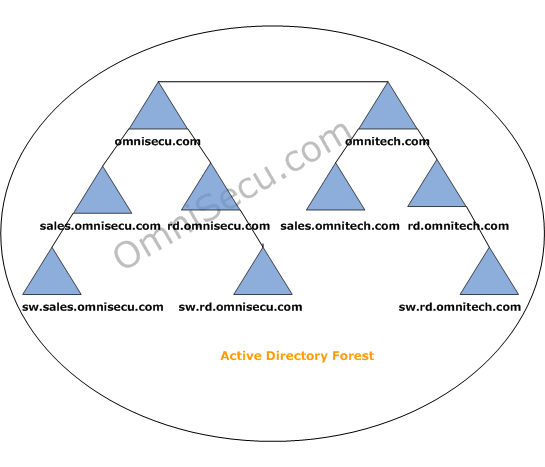
What is an Active Directory (AD) Tree?
An Active Directory tree is a collection of Active Directory domains that begins at a single root and branches out into peripheral, child domains. Domains in an Active Directory tree share the same namespace. An Active Directory forest is a collection of Active Directory trees, similiar to a real world forest.
Following figure explains an Active Directory Tree.
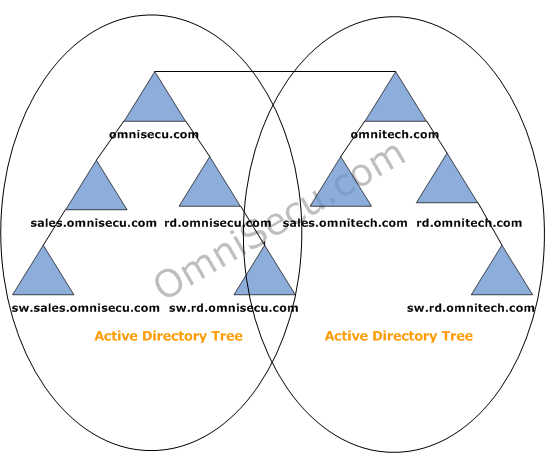
An Active Directory domain tree forms a contiguous namespace. The domains in the Active Directory tree share a boundary with each other. When a new domain is added under another domain in an Active Directory tree, a parent-child relation is formed between the existing domain and the newly added domain.
No two tree in an Active Directory forest can share the same name space. For example, the first tree in the above Active Directory forest is omnisecu.com and the second tree in the above Active Directory
forest is omnitech.com. The child domains of omnisecu.com are
sales.omnisecu.com and rd.omnisecu.com. The child domain of
sales.omnisecu.com is sw.sales.omnisecu.com
What is Active Directory Domain?
The primary unit of logical structure in Active Directory is the Active Directory domain. Active Directory domain is also an Active Directory container which can hold a large number of other Active Directory objects like users, computers, printers, shared folders, groups etc.
Active Directory domain allow centralized management and control of Active Directory objects (Active Directory users, computers, printers, shared folders, groups etc). Every object within an Active Directory domain is controlled by the same security policies and access restrictions.
An Active Directory domain is the security boundary that controls authentication of users, access to resources available in the Active Directory, and trusts with other Active Directory domains.
First domain is implemented when Active Directory is installed on the first domain controller in that domain.
Following figure explains the relation between an Active Directory forest, Active Directory tree and an Active Directory domain.
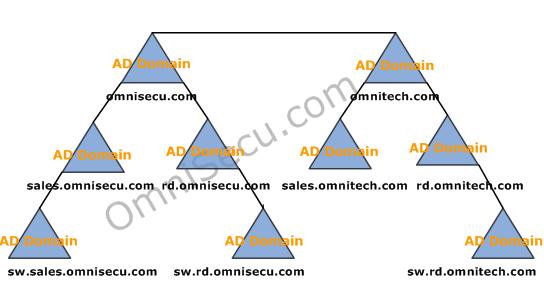
What is a Domain Controller?
Active Directory Domain Controllers (DC) are servers (Microsoft Windows 2000 server, Microsoft Windows 2003 server or Microsoft Windows 2008 server) that has the Active Directory services installed. When you install Active Directory any of Microsoft Server Operating System, you are promoting it to an Active Directory Domain Controller (DC).
An Active Directory domain should contain at least one Domain Controller (DC). Additional Domain controllers are required when the network start growing, for load balancing and redundancy.
In an Active Directory domain, each of the domain controllers act as an equal peer, holding a read/write copy of the Active Directory database and they have the capability to send updates to other domain controllers in the Active Directory domain.
An Active Directory domain controller (DC) can be authoritative for only one domain and it is not possible to host multiple domains on a single Domain Controller (DC).
You can promote a Windows 2003 stand-alone server to a Domain Controller by using a wizard named "dcpromo.exe". Click the following link to learn how to install Active Directory.
What is Organizational Unit (OU)?
Organizational Unit (OU) is a special container of Active Directory, which is used to organize Active Directort objects within a domain into administrative groups or simply an organizational unit (OU) is a logical group of Active Directory
objects. An OU can contain objects like user accounts, groups,
computers, printers, file shares, and other OUs from the same domain.
Organizational Units (OUs) can be used to divide a domain into groups that mirror
the functional or physical divisions within an organization.
Organizational units are limited within a single domain. It is possible
to implement OU hierarchy within each Active Directory Domain.
Organizational units can be created within Active Directory
domains as folders in a file system. Once you have created an
Organizational Unit (OU) hierarchy which fit your company's business
structure, you can store objects in OUs just like files inside folders.
By creating a hierarchy, the difficulty of administration of Active Directory objects can be reduced to a great extent.
The administration
of each Organizational Unit (OU) can be delegated to different
administrators. For a large organization spanned over different geographical
location it is better to give the permission to local administrators
to manage individual Organizational Unit (OU) (creating users, creating
groups, resetting forgotten passwords etc).
Another feature of Organizational Units (OUs) is that you can assign Group Policies to the users and computers in each OU. In Active Directory, Group Policies can be assigned only to Active Directory domains, Active Directory sites and Organizational Units (OUs).
Active Directory Trusts
Active Directory Trust relationship is a logical link which allows a domain to
access another domain, or a forest to access another forest. Trusts
which are created automatically are called as implicit Trusts and the
trusts which are created manually are called as Explicit Trusts.
The following are the characteristics of Windows 2003 Trusts.
• Active Directory Trusts can be created manually (explicitly) or automatically (implicitly).
• Active Directory Trusts can be either transitive or non transitive. A transitive trust extends the trust relationships with other domains and a nontransitive does not allow the trust to flow to any other domains in the forest.
• Active Directory Trusts can be one-way or two-way.
Active Directory Trust Types
Parent-child Trust: Parent-child Trust is an implicitly established, two-way, transitive trust when you add a new child domain to a tree.
Tree-root Trust: Tree-root Trust is an implicitly established, two-way, transitive trust when you add a new tree root domain to a forest.
Shortcut Trust:
Shortcut Trust is an explicitly created, transitive trust between two
domains in a forest to improve user logon times. Shortcut Trust will
make a trust path shorter between two domains in the same forest. The
Shortcut Trust can be one-way or two-way.
External Trust: External Trust is explicitly created, non-transitive trust between Windows Server 2003 domains that are in different forests or between a Windows Server 2003 domain and Windows NT 4 domain. The External Trust can be one-way or two-way.
Realm Trust: Realm Trust is explicitly created transitive or non-transitive trust between a non Windows Kerberos realm and a Windows Server 2003 domain. This trust helps to create trust relationship between Windows Server 2003 domain and any Kerberos version 5 realm. The Realm Trust can be and one-way or two-way.
Forest Trust:
Forest Trust is explicitly transitive (between two forests) created
trust between two forest root domains. The Forest Trust can be one-way
or two-way.
What is Active Directory Schema?
The Active Directory schema is a component of Active Directory which contains rules for object creation within an Active Directory forest. The Active Directory schema is a list of definitions about Active Directory objects and information about those objects that are stored in Active Directory.
The schema is the blueprint of Active Directory and schema defines what kinds of objects can exist in the Active Directory database and attributes of those objects.
Active Directory Classes, Objects and Attributes
The information in the Active Directory
is represented as Objects, and there is an object for each user,
computer, printer etc. Object of the same type belong to same class.
Example: All user objects belong to class "user", all computer objects belong to class “computer” and all printer objects belong to class "printQueue".
The information in
an object is stored as Attributes (Properties), which the
corresponding class supports. Attributes define various information that
a class can contain.
The process
of creating an object from a class is called instantiation, and an
object created from a class is called an instance of that class.
Example: You have created a user called jerome.h in the Active Directory. The user object jerome.h is an instance of the Active Directory class "user".
Classes are categorized as abstract, structural and auxiliary classes.
• Abstract classes: Abstract classes provide attributes that flow through the hierarchy, but they cannot be used to instantiate an object. Abstract classes can inherit from other classes and can have attributes defined on them directly, but you cannot create (instantiate) and object of an abstract class.
• Structural classes: Structural classes can be instantiated into objects and can contain additional attributes that are not inherited from the other class types. The user and group classes are the examples of structural classes.
• Auxiliary classes. Auxiliary classes
provide attributes that extend a structural class, but they cannot be
used to form a structural class by themselves or instantiate an object.
Windows 2003 Active Directory Installation - How to configure static IP address
In this lesson, you will learn how to configure a static IP address on a Windows 2003 Enterprise Server.
Active Directory can be installed on a Windows 2003 Server. Here in this example, we are going to configure Active Directory on a Windows 2003 Enterprise Server. It is always better to configure a static IP address on the server which is going to be an Active Directory domain controller. To configure a static IP address on Windows 2003 Enterprise Server,
right click "My Network Places" and select "Properties" from the popup
menu. In the "Network Connections" explorer window, right Click "Local
Area Connection" and select "Properties".
"Local Area Connection Properties" dialog box will open.
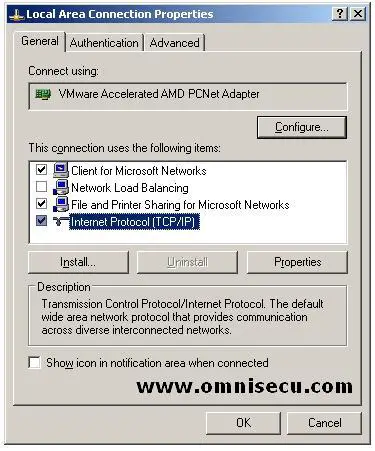
Select "Internet Protocol (TCP/IP)" and click Properties Button.
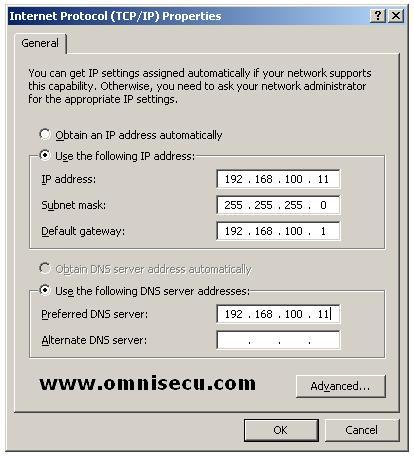
Fill the fields inside "Internet
Protocol (TCP/IP)" dialog box with the required values and click "OK".
Click "Close" in the "Local Area Connection Properties" dialog box.
You have configured a static IP address on a Windows 2003 Enterprise Server. Click "Next" to continue.
How to install Domain Name System (DNS)
Domain Name System (DNS) is a mandatory service for Windows Active Directory and with out Domain Name System (DNS) Windows Active Directory will not work properly. Windows Active Directory uses Domain Name System (DNS) for name resolution. It is always better to install the Domain Name System (DNS) service before Active Directory installation. In this example we are going to install the Domain Name System (DNS) and the Active Directory services in same server.
To install Domain Name System (DNS) service open "Add or Remove Programs" applet from the Control Panel (Start > Control Panel > Add or Remove Programs).
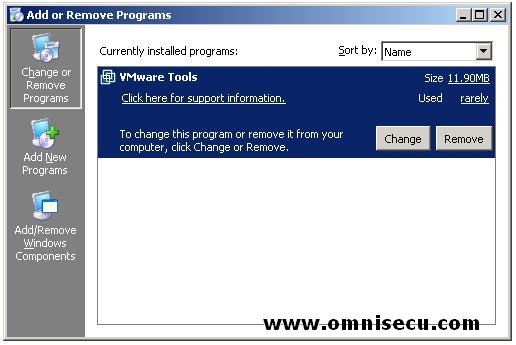
Click "Add/Remove Windows Components" button (Left panel, Bottom-most). This will fire up Windows Components Dialog box.
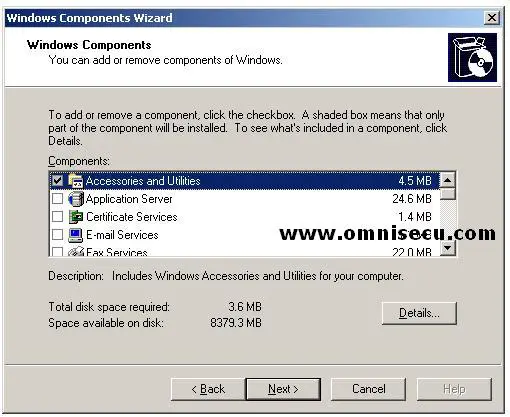
Scroll down the list box inside "Windows Components" screen, and find "Networking Services".
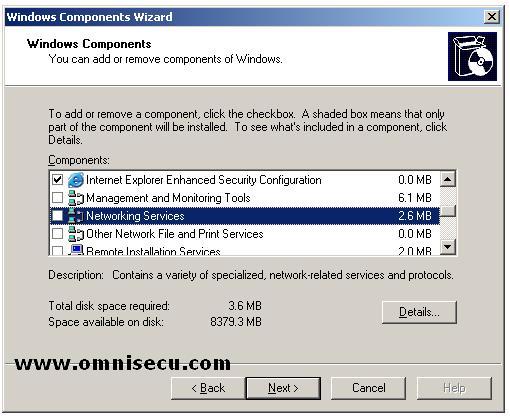
Highlight "Networking Services" and click "Details" button.
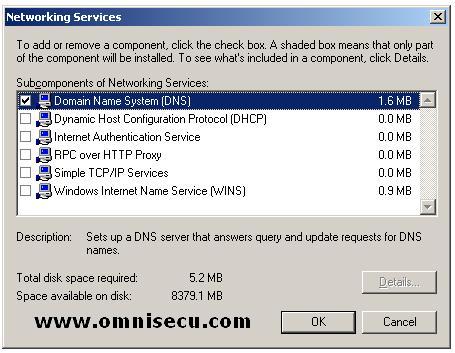
Check the "Domain Name System (DNS)" checkbox inside "Networking Services" dialog box and Click "OK".
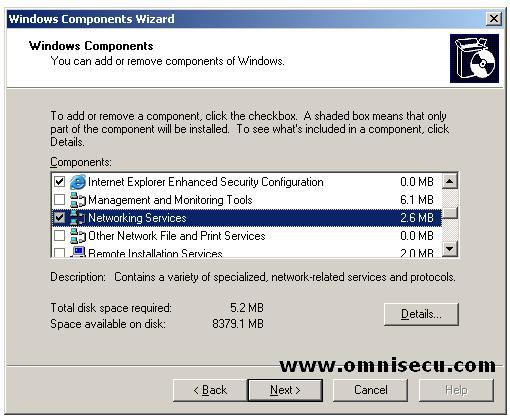
Inside "Windows
Components" screen, you can now see "Netorking Services" selected and
the colour of the checkbox is grey. This means that only one Networking
Component is selected (Domain Name System (DNS)) from many available
components. Click "Next". You may require Windows 2003 Enterprise Server installation CD to copy Domain Name System (DNS) installation files. The files which are required to install Domain Name System (DNS) can be found inside "i386" folder inside Windows 2003 Enterprise Server installation CD. A "Copy Error" dialog box may be displayed and you can click the "Browse" button to select i386 folder inside Windows 2003 Enterprise Server installation CD.
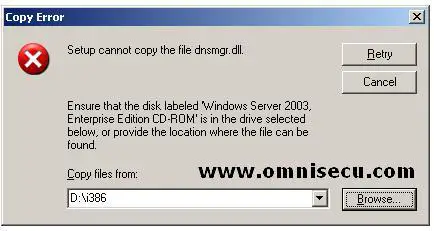
In the "Locate File" Dialog box, locate i386 folder and click "Open".
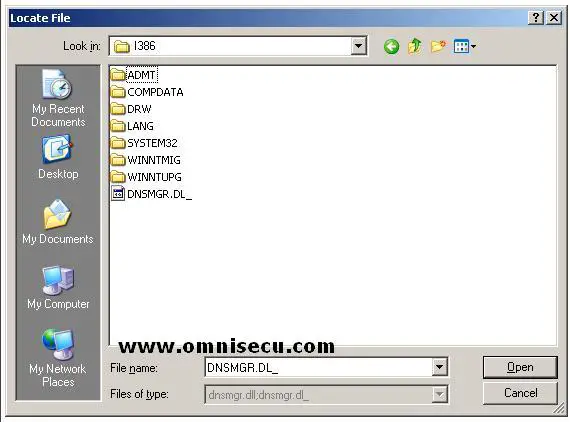
Click "Retry" button in the "Copy Error" dialog box.
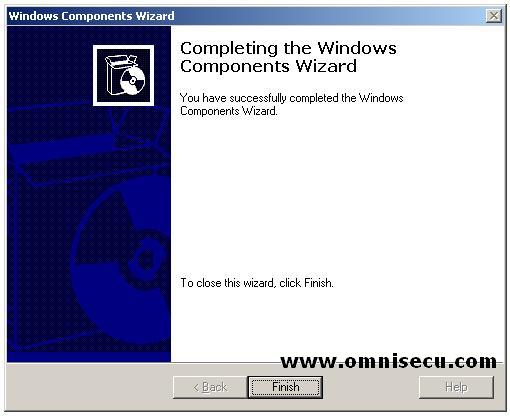
"Completing the Windows Components
Wizard" screen will be displayed and now you have installed Domain Name
System (DNS) service on a Windows 2003 Enterprise Server.
Windows 2003 Active Directory Installation - Running Dcpromo
Dcpromo is a utility which comes with Windows 2003 Server products which is used to Install and uninstall Active Directory Services. The dcpromo executable can be located inside %systemroot%/system32 folder.
To run dcpromo, goto Start > Run, type dcpromo.
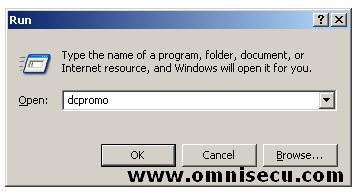
Click "OK".
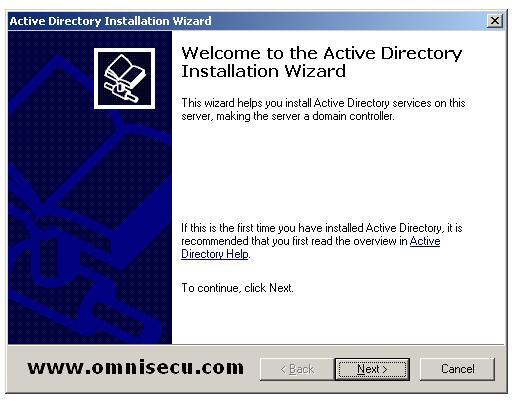
Click "Next" to move to "Operating System Compatibility" dcpromo wizard screen.
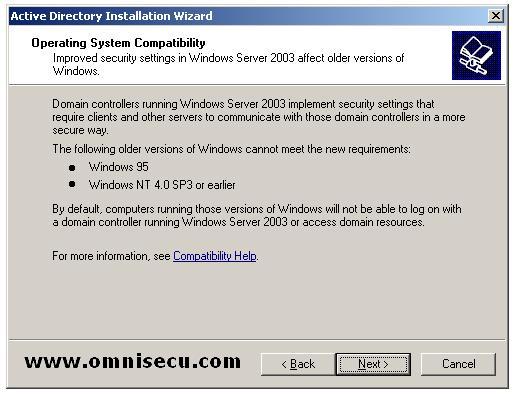
"Operating System
Compatibility" dcpromo wizard screen shows some warning about using old
versions of Windows. Click "Next" to move to "Domain Controller Type" dcpromo wizard screen.
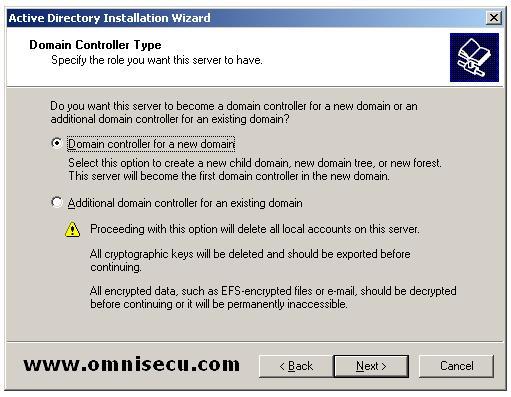
In "Domain Controller Type" dcpromo wizard screen, you have to identify whether you are going to create a new domain or an additional domain controller for an existing domain. Select "Domain Controller for a new domain" and click "Next".
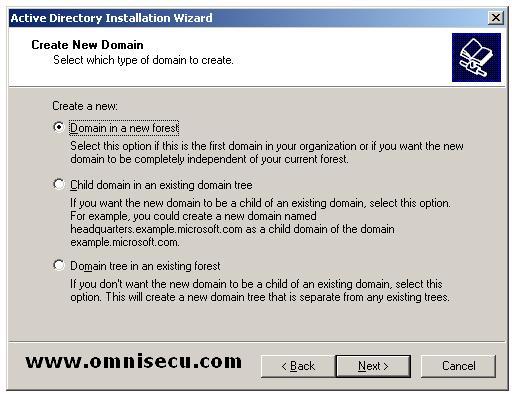
In "Create new Domain" screen, you can select the new domain as a domain in a new Active Directory forest, or as a child domain in an already created Active Directory Tree or as a Domain Tree in an already created Active Directory forest. Select "Domain in a new forest" since you are going to create a new forest. Click "Next".
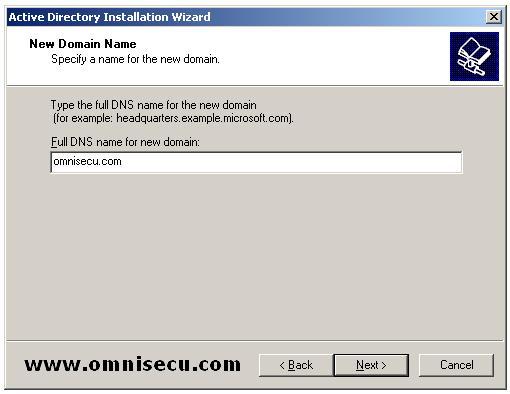
Inside "New Domain Name" screen, enter the name of the new Active Directory domain you are going to create and click "Next".
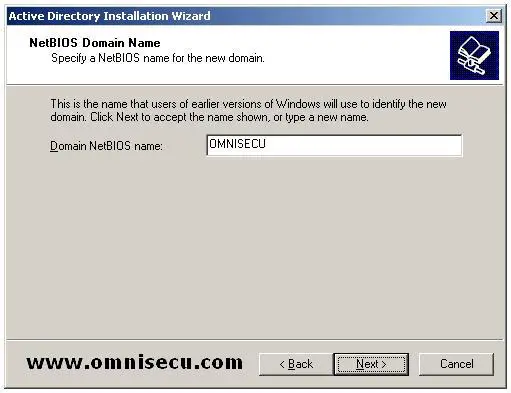
"NetBIOS Domain Name" screen will display the NetBIOS name of the Active Directory domain you are going to create. NetBIOS name has a flat naming structure. Click "Next".
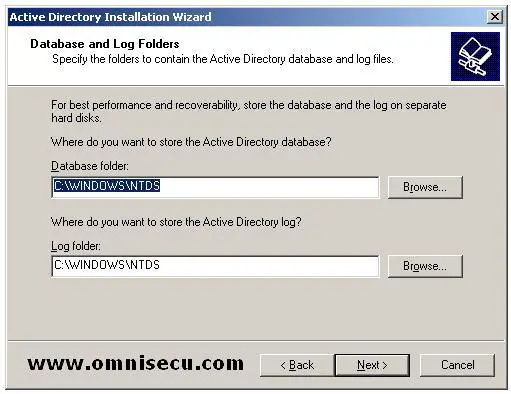
"Database and Log folders" screen will display the physical location of Active Directory database and Active Directory log files. Click "Next".
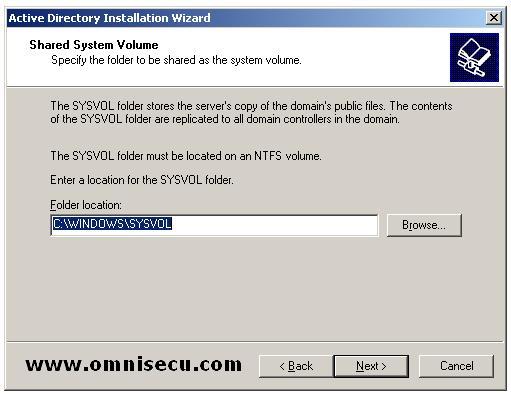
"Shared System
Volume" screen will display the physical location of the "SYSVOL"
folder, which stores the servers copy of the public files.
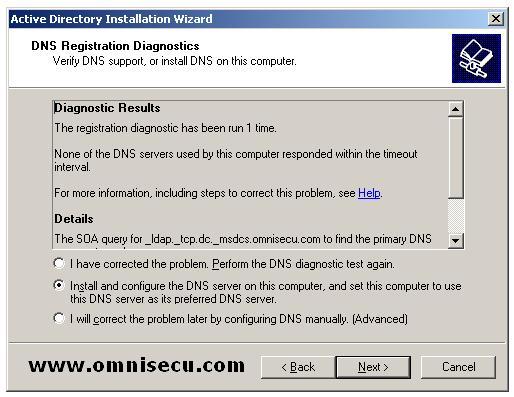
"DNS registration
Dagnostics" screen, Select "Install and configure the DNS server on
this computer, and set this computer to use this DNS server as its
preferred DNS server" radio button. Click "Next".
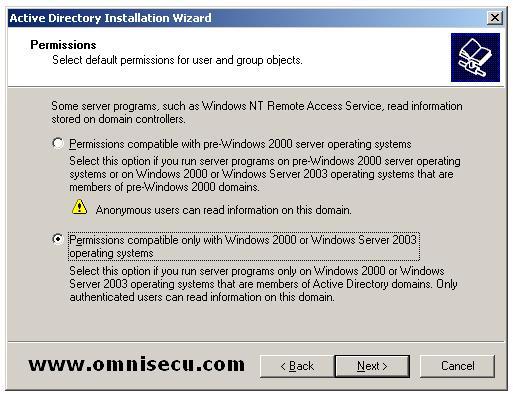
In "Permissions"
screen you can decide whether you require compatibility with
pre-Windows 2000 machines. You will have better security if you select
"Permissions compatible only with Windows 2000 or Windows Server 2003
operating systems."
If you select the first radio button
"Permissions Compatible with pre-Windows 2000 server operating
systems" Anonymous Logon group and the Everyone security groups will
be added to the Pre-Windows 2000 Compatible Access group . To prevent
members of the Anonymous Logon group from getting read access to user
and group information, choose the second option, "Permissions
compatible only with Windows 2000 or Windows Server 2003 operating
systems" radio button. Click "Next".
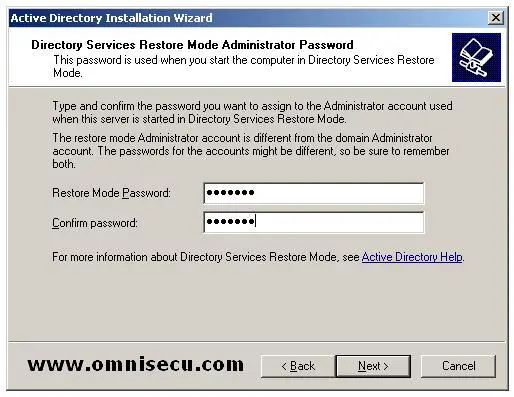
In "Directory Services Restore Mode Administrator Password" screen, you will be prompted to enter Directory Services Restore Mode Administrator Password. This password is required when you enter the Active Directory server as Directory Services Restore Mode. Click "Next".
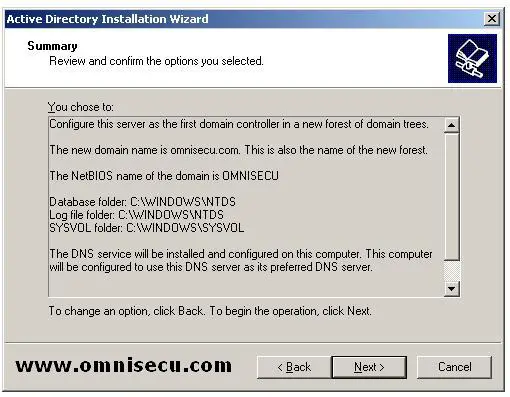
In the summary screen, you can see the summary of your selections. Click "Next" to start begin the Active Directory configuration.
Now the configuration of Active Directory is started and you can see a dialog box with an animated image. It will take a few minutes to complete the Active Directory configuration.
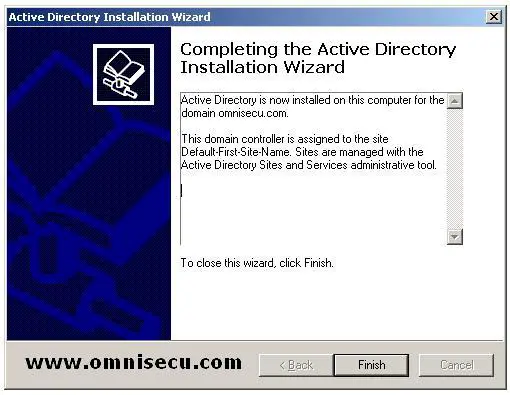
Once the Active Directory configuration is over you can see the "Completing Active Directory Installation Wizard". Click "Finish".
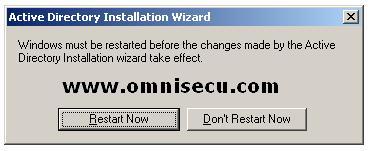
A server restart prompt will be displayed and you need to restart the server to complete the Active Directory Installation Wizard. Once you restart the server, you server will be the Domain Controller for the domain "omnisecu.com".
How add a computer to an Active Directory Domain?
If you want a computer to be a member of an Active Directory domain, you should add that computer to the Active Directory Domain. Following steps will make the stand-alone server SERV02, a member of Active Directory domain omnisecu.com.
Before proceeding, make sure you have connectivity from computer SERV02 to SERV01.omnisecu.com, by pinging to 192.168.1.11, which is the IP address of Active Directory domain controller SERV01.omnisecu.com.
Configure SERV02 TCP/IP configuration to use the Domain Name System (DNS) server installed on SERV01.omnisecu.com for host name resolution.
To configure the computer SERV02 to use the Domain Name System (DNS)
server running on SERV01.omnisecu.com, open the TCP/IP properties of
SERV02.
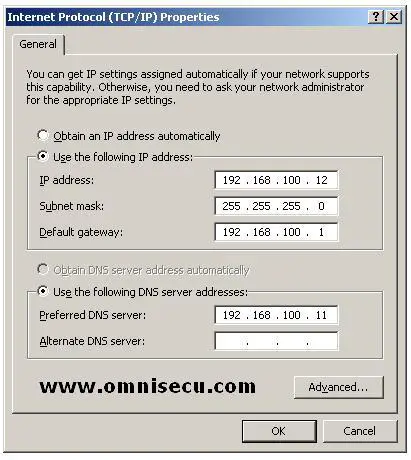
In the preferred DNS server field, enter the IP address of computer 192.168.100.11, which is the IP address of the domain controller
SERV01.omnisecu.com. We have the Domain Name System (DNS) services also
running on SERV01.omnisecu.com. Now SERV02 will make use of the Domain
Name System (DNS) services running on SERV01.omnisecu.com for name resolution.
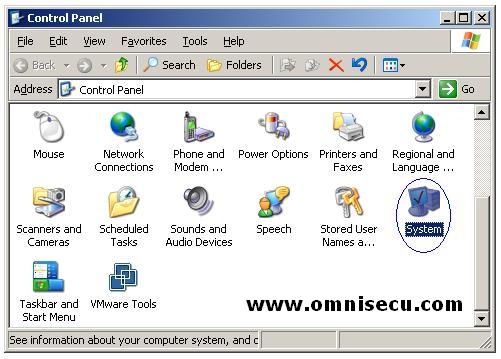
After configuring
the TCP/IP settings in SERV02, open the "System" applet from the Control
Panel by choosing the path Start > Control Panel > System. (You
can also open the "System" applet by right clicking "My Computer" and
selecting the "Properties" from the context menu). Click the "Computer Name" tab.
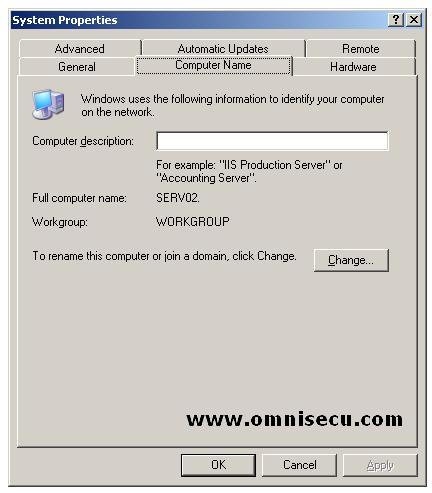
Click the "Change" button.
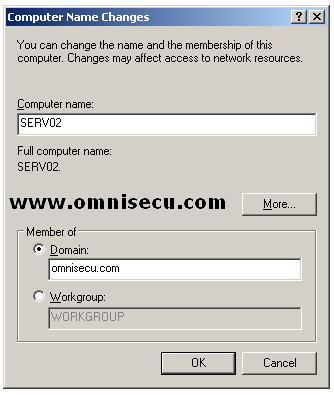
Inside Computer name tab, select the "Domain" radio button and enter the Active Directory domain name, to which you are trying to add your computer.
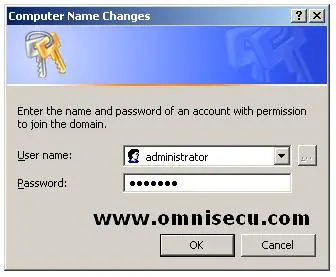
Enter the Administrator account user id and password at the domain level, Click "OK".
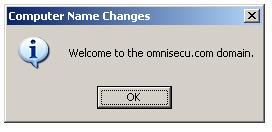
A welcome message dianlog box will be displayed and a prompt to restart the server SERV02 also will be displayed when you click the OK button at the welcome message.
Click "OK" to restart the server. SERV02 is now a member of Active Directory domain omnisecu.com and the Fully Qualified Domain Name (FQDN) of SERV02 now is SERV02.omnisecu.com
Active Directory files and their functions
Ntds.dit
Ntds.dit is the main AD database file. NTDS stands for NT Directory Services. The DIT stands for Directory Information Tree. The Ntds.dit file on a particular domain controller contains all naming contexts hosted by that domain controller, including the Configuration and Schema
naming contexts. A Global Catalog server stores the partial naming
context replicas in the Ntds.dit right along with the full Domain naming
context for its domain.
Edb.log
Edb.log is a transaction log. Any changes made to objects in Active Directory
are first saved to a transaction log. During non-peak times in CPU
activity, the database engine commits the transactions into the main
Ntds.dit database. This ensures that the database can be recovered in
the event of a system crash. Entries that have not been committed to
Ntds.dit are kept in memory to improve performance. Transaction log files
used by the ESE (Extensible Storage Engine is an Indexed Sequential
Access Method (ISAM) data storage technology from Microsoft. ESE is the
core of Microsoft Exchange Server and Active Directory.) engine are always 10MB.
Edbxxxxx.log
These are auxiliary transaction logs used to store changes if the main Edb.log file gets full before it can be flushed to Ntds.dit. The xxxxx stands for a sequential number in hex. When the Edb.log file fills up, an Edbtemp.log file is opened. The original Edb.log file is renamed to Edb00001.log, and Edbtemp.log is renamed to Edb.log file, and the process starts over again. Excess log files are deleted after they have been committed. You may see more than one Edbxxxxx.log file if a busy domain controller has many updates pending.
Edb.chk
Edb.chk is a
checkpoint file. It is used by the transaction logging system to mark
the point at which updates are transferred from the log files to
Ntds.dit. As transactions are committed, the checkpoint moves forward in
the Edb.chk file. If the system terminates abnormally, the pointer
tells the system how far along a given set of commits had progressed
before the termination.
Res1.log and Res2.log
Res1.log and Res2.log are reserve log files. If the hard drive fills to capacity just as the system is attempting to create an Edbxxxxx.log file, the space reserved by the Res log files is used. The system then puts a dire warning on the screen prompting you to take action to free up disk space quickly before Active Directory gets corrupted. You should never let a volume containing Active Directory
files get even close to being full. File fragmentation is a big
performance thief, and fragmentation increases exponentially as free
space diminishes. Also, you may run into problems as you run out of
drive space with online database defragmentation (compaction). This can cause Active Directory to stop working if the indexes cannot be rebuilt.
Temp.edb
This is a scratch
pad used to store information about in-progress transactions and to
hold pages pulled out of Ntds.dit during compaction.
Schema.ini
This file is used to initialize the Ntds.dit during the initial promotion of a domain controller. It is not used after that has been accomplishedWhat is Active Directory Naming Context or Directory Partition
All of the objects in the Active Directory forest are represented in the Directory Tree. A Directory Tree is a hierarchy of objects and containers in a directory
that can be viewed graphically as an upside-down tree, with the root
object at the top. A tree shows how objects are connected in terms of
the path from one object to another.
The Directory Tree of Active Directory tree is partitioned to allow sections to be distributed (replicated) to domain controllers in different domains within the forest. Each domain controller stores a copy of a specific part of the directory tree, called a “Naming Context” also know as Directory Partition. “Naming Context” is replicated as a unit to other domain controllers in the forest that contain a replica of the same sub tree. A “Naming Context” is also called a Directory Partition.
In Active Directory, a single server always holds at least three naming contexts:
Schema Naming Context
Schema
Naming Context contains definitions of objects that can be created in
the forest and the attributes those objects can have. Objects in the schema partition must be replicated to all domain controllers in all domains in the forest.
Configuration Naming Context
Configuration
Naming Context contains objects that represent the logical structure of
the forest, including the domain structure and replication topology.
Objects in the configuration partition must be replicated to all domain controllers in all domains in the forest.
Domain Naming Context
Domain Naming Context contains all of the objects stored in a domain. Objects in the domain partition can be replicated only to domain controllers within the domain.What is Active Directory Replication?
Windows 2003 Active Directory has a distributed directory structure and stores objects (users, computers, printers etc). Objects which are stored in Active Directory are distributed different domain controllers in a forest. Active Directory replication is the process by which the changes that originate on one domain controller are automatically transferred to other domain controllers in the forest.
Replication is a necessary factor in Active Directory to ensure
Fault tolerance: If one domain controller fails, the Active Directory database is still available from other domain controllers, which store the same information.
Load balancing: When many workstations are accessing Active Directory, the information they are requesting is retrieved faster when there is more than one domain controller to provide it.
Proximity of information: Workstations get the information from a local domain controller instead of across a slow WAN link.
Replication process ensures that changes made to a replica on one domain controller are synchronized to replicas on all other domain controllers within the domain.
The following actions trigger replication between domain controllers:
• Creating an object (When adding a user or a computer)
• Modifying an object
• Moving an object
• Deleting an object
• Modifying an object
• Moving an object
• Deleting an object
You can use several different methods to force replication.
• Using the Active Directory Sites and Services MMC snap-in (Dssite.msc)
• Using Repadmin
• Using Replmon
• Using a script
• Using Repadmin
• Using Replmon
• Using a script
There are two types of Active Directory Replication.
1) Intrasite (Replication within a site)
2) Intersite (Replication between sites).
2) Intersite (Replication between sites).
The following table compares Intrasite and Intersite replication.
Function
|
Intrasite Replication
|
Intersite Replication
|
Compression
|
To save CPU time, replication data is not compressed.
|
To save WAN bandwidth, replication data greater than 50 kilobytes (KB) is compressed.
|
Replication model
|
To reduce replication latency, replication partners notify each other when changes need to be replicated and then pull the information for processing.
|
To save WAN bandwidth, replication partners do not notify each other when changes need to be replicated.
|
Replication frequency
|
Replication partners poll each other periodically.
|
Replication
partners poll each other at specified intervals, only during
scheduled periods. If updates are necessary, operations are scheduled
to pull the information for processing.
|
Transport protocols
|
Remote procedure call (RPC).
|
IP or Simple Mail Transport Protocol (SMTP).
|
http://www.omnisecu.com/windows-2003/index.htm

0 comments
Post a Comment