Microsoft Outlook
![]() Microsoft Outlook fits into several application categories. It is a personal information manager (PIM) because it functions as a personal calendar, scheduler, contact manager, and task manager. It is also a messaging application because it includes a powerful e-mail program and forms program. And finally, it is a groupware application because it can access Exchange Server public folders and enables calendars, schedules, contact information, and task information to be used in a group context. All of this functionality exists through a single, integrated, desktop environment.
Microsoft Outlook fits into several application categories. It is a personal information manager (PIM) because it functions as a personal calendar, scheduler, contact manager, and task manager. It is also a messaging application because it includes a powerful e-mail program and forms program. And finally, it is a groupware application because it can access Exchange Server public folders and enables calendars, schedules, contact information, and task information to be used in a group context. All of this functionality exists through a single, integrated, desktop environment.
![]() Outlook 2003 is part of the Microsoft Office 2003 suite and as such is tightly integrated with the other Office applications, though it can also be purchased as a stand-alone product. Outlook is fully MAPI compliant.
Outlook 2003 is part of the Microsoft Office 2003 suite and as such is tightly integrated with the other Office applications, though it can also be purchased as a stand-alone product. Outlook is fully MAPI compliant.
| Note |
|
![]() Some of the improvements in Outlook 2003 over previous versions of the Outlook client include:
Some of the improvements in Outlook 2003 over previous versions of the Outlook client include:
![]() Cache mode operation When configured, allows Outlook 2003 to work from a local cache of the user’s Exchange mailbox, which is stored in an OST file on the local computer. The Offline Address List is also made available. The local cache is refreshed periodically from the Exchange server.
Cache mode operation When configured, allows Outlook 2003 to work from a local cache of the user’s Exchange mailbox, which is stored in an OST file on the local computer. The Offline Address List is also made available. The local cache is refreshed periodically from the Exchange server.
![]() RPC over HTTP Provides a means for Outlook 2003 users to make secure connections over the Internet to an Exchange organization without the need for a VPN.
RPC over HTTP Provides a means for Outlook 2003 users to make secure connections over the Internet to an Exchange organization without the need for a VPN.
![]() Smart change synchronization Allows for changes to an item to require only synchronization of the changes, versus the entire item as with previous versions of Outlook.
Smart change synchronization Allows for changes to an item to require only synchronization of the changes, versus the entire item as with previous versions of Outlook.
![]() Incremental Change Synchronization (ICS) check-pointing Using this method of synchronization prevents the resending of data that was successfully sent if network connectivity is interrupted during a synchronization event. In this event, Outlook 2003 will simply continue the synchronization event where it left off once connectivity is restored.
Incremental Change Synchronization (ICS) check-pointing Using this method of synchronization prevents the resending of data that was successfully sent if network connectivity is interrupted during a synchronization event. In this event, Outlook 2003 will simply continue the synchronization event where it left off once connectivity is restored.
![]() Skip Bad Items To prevent the failure of the synchronization process, as occurred in previous versions of Outlook, Outlook 2003 will skip and log all bad or malformed items that are found on the server during a synchronization event. Items that are marked as infected by a virus scanner that integrates with Exchange Server 2003 will also be skipped.
Skip Bad Items To prevent the failure of the synchronization process, as occurred in previous versions of Outlook, Outlook 2003 will skip and log all bad or malformed items that are found on the server during a synchronization event. Items that are marked as infected by a virus scanner that integrates with Exchange Server 2003 will also be skipped.
![]() Pre-synchronization reporting MAPI compression Using MAPI compression allows for much faster communication between server and client. This compression is applied to the message header, message body, and any attachments.
Pre-synchronization reporting MAPI compression Using MAPI compression allows for much faster communication between server and client. This compression is applied to the message header, message body, and any attachments.
![]() PST/OST enhancements As mentioned previously, PST and OST files now use the Unicode format and can exceed the previous size limit of 2 GB.
PST/OST enhancements As mentioned previously, PST and OST files now use the Unicode format and can exceed the previous size limit of 2 GB.
![]() Send/Receive groups improvements Additional configuration and customization options have been provided for users using Send/Receive groups to enhance their Outlook experience.
Send/Receive groups improvements Additional configuration and customization options have been provided for users using Send/Receive groups to enhance their Outlook experience.
 Architectural Design
Architectural Design
![]() Microsoft Outlook is designed to be a desktop information manager. This means it integrates personal and groupware tools, as well as their information, in a unified manner. This goal was achieved by including the following design features:
Microsoft Outlook is designed to be a desktop information manager. This means it integrates personal and groupware tools, as well as their information, in a unified manner. This goal was achieved by including the following design features:
![]() Single application, multiple functionality From a single interface, users can execute numerous programs such as e-mail, calendar, contact list, and task list.
Single application, multiple functionality From a single interface, users can execute numerous programs such as e-mail, calendar, contact list, and task list.
![]() Integrated user interface All the tools in Outlook are seamlessly integrated. For example, Outlook includes a feature called the Outlook Bar. This is a navigation tool that creates shortcuts to a user’s e-mail Inbox, calendar, contacts, tasks, and folders. Outlook, as a MAPI program, provides a single address book that can be used for e-mail, phone dialing, faxing, and other functions. The Outlook interface permits users to access both local file folders and Exchange public folders.
Integrated user interface All the tools in Outlook are seamlessly integrated. For example, Outlook includes a feature called the Outlook Bar. This is a navigation tool that creates shortcuts to a user’s e-mail Inbox, calendar, contacts, tasks, and folders. Outlook, as a MAPI program, provides a single address book that can be used for e-mail, phone dialing, faxing, and other functions. The Outlook interface permits users to access both local file folders and Exchange public folders.
![]() Custom forms using Office 2003 One example of Outlook’s tight integration with Office 2003 is its ability to create and send forms that include objects created in any of the Office 2003 applications. For instance, an expense report form that includes an Excel spreadsheet can be created. Because of Microsoft object technology (see note below), the spreadsheet contained in the form will not be merely rows and columns but will include the Excel code to execute the functions of the spreadsheet. The form’s users can enter their numbers, have the spreadsheet calculate them, and then have the form automatically sent to a designated person. Outlook, along with Microsoft Office 2003, enables the creation of instant groupware applications.
Custom forms using Office 2003 One example of Outlook’s tight integration with Office 2003 is its ability to create and send forms that include objects created in any of the Office 2003 applications. For instance, an expense report form that includes an Excel spreadsheet can be created. Because of Microsoft object technology (see note below), the spreadsheet contained in the form will not be merely rows and columns but will include the Excel code to execute the functions of the spreadsheet. The form’s users can enter their numbers, have the spreadsheet calculate them, and then have the form automatically sent to a designated person. Outlook, along with Microsoft Office 2003, enables the creation of instant groupware applications.
| Note |
|
 Features of Microsoft Outlook
Features of Microsoft Outlook
![]() Microsoft Outlook includes some very powerful messaging, groupware, and personal productivity features. Tables 7.1, 7.2, and 7.3 describe many of those features.
Microsoft Outlook includes some very powerful messaging, groupware, and personal productivity features. Tables 7.1, 7.2, and 7.3 describe many of those features.
|
|
|
|
|---|---|---|
|
|
|
|
|
|
| |
|
|
| |
|
|
| |
|
|
| |
|
|
| |
|
|
| |
|
|
| |
|
|
|
|
|
|
|
|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
|
|
|
|
|
|
|
|
|---|---|---|
|
|
|
|
|
|
| |
|
|
|
|
|
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
|
|
|
|
|
|
| |
|
|
| |
|
|
| |
|
|
| |
|
|
| |
|
|
| |
|
|
| |
|
|
| |
|
|
|
|
|
|
|
|
 Installing and Configuring Outlook 2003
Installing and Configuring Outlook 2003
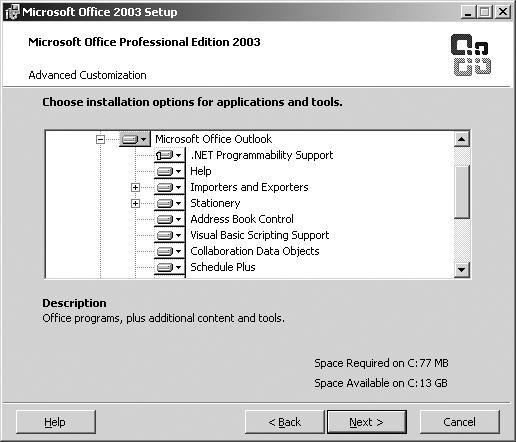
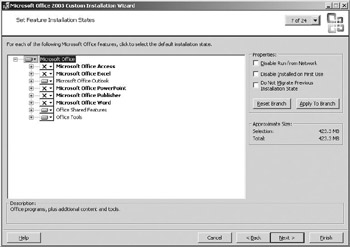
![]() As with most other Windows programs, Outlook 2003 is installed using a fairly intuitive wizard that lets you choose the specific components of the program that you want installed (see Figure 7.14).
As with most other Windows programs, Outlook 2003 is installed using a fairly intuitive wizard that lets you choose the specific components of the program that you want installed (see Figure 7.14).
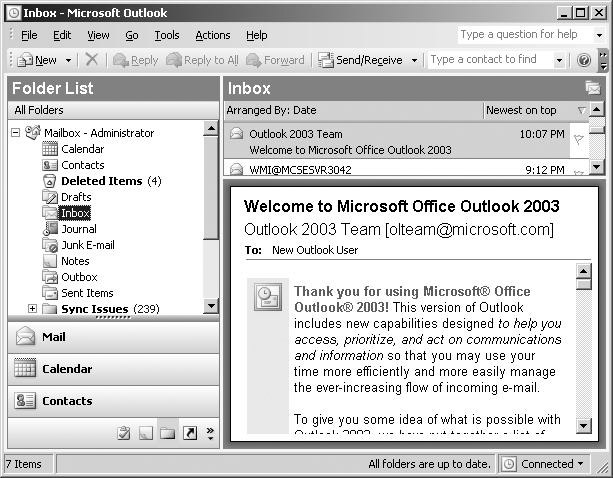
![]() In addition to the new look that Outlook 2003 sports (seen in Figure 7.15), it has some nice new features that you will need to be aware of. First and foremost is the ability of Outlook 2003 to operation in a cache mode, where the Outlook client does not require constant connectivity to its Exchange server. While you may, at first, be tempted to think this is nothing new and is in fact just a new name for the familiar offline mode of operation, this is not the case. The plot thickens when you learn that both cache mode and offline mode use OST (offline storage files) to facilitate their operation.
In addition to the new look that Outlook 2003 sports (seen in Figure 7.15), it has some nice new features that you will need to be aware of. First and foremost is the ability of Outlook 2003 to operation in a cache mode, where the Outlook client does not require constant connectivity to its Exchange server. While you may, at first, be tempted to think this is nothing new and is in fact just a new name for the familiar offline mode of operation, this is not the case. The plot thickens when you learn that both cache mode and offline mode use OST (offline storage files) to facilitate their operation.
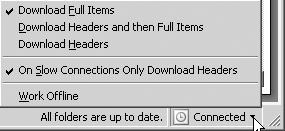
![]() The difference between the new cache mode and the existing offline mode is that users who are working in cache mode automatically have their OST file updated through a synchronization process to the user’s mailbox server. As well, all standard Exchange features, such as mail, calendaring, free/busy information, and address lists, are available to a user when the user is using cache mode. A status indicator in the bottom of the Outlook window shows the current status of Outlook, as seen in Figure 7.15. By clicking on the status, you can configure the mode of operation that Outlook will use, as seen in Figure 7.16.
The difference between the new cache mode and the existing offline mode is that users who are working in cache mode automatically have their OST file updated through a synchronization process to the user’s mailbox server. As well, all standard Exchange features, such as mail, calendaring, free/busy information, and address lists, are available to a user when the user is using cache mode. A status indicator in the bottom of the Outlook window shows the current status of Outlook, as seen in Figure 7.15. By clicking on the status, you can configure the mode of operation that Outlook will use, as seen in Figure 7.16.
| Note |
|
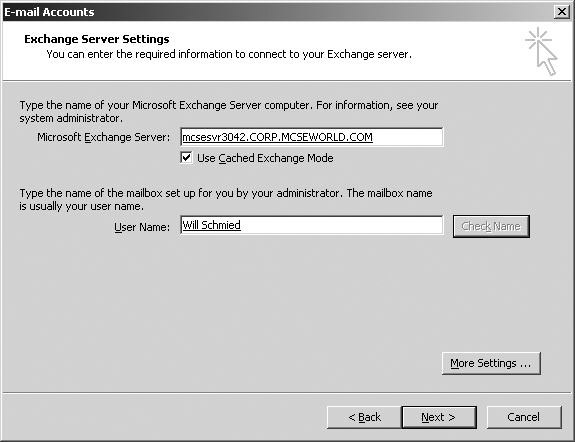
![]() Because the cache mode of operation is new to Outlook 2003 when paired up with Exchange Server 2003, your users will likely want some help in getting it set up correctly on their client workstations. The default state for all newly created Outlook 2003 accounts is the cache mode of operation, thus improving the user’s experience and reducing the load placed on the Exchange servers. Messages are still available on the Exchange server, but they are cached locally for the user. You do, however, when creating the account to connect to the Exchange server, have the option to configure how Outlook is initially configured, as seen in Figure 7.17.
Because the cache mode of operation is new to Outlook 2003 when paired up with Exchange Server 2003, your users will likely want some help in getting it set up correctly on their client workstations. The default state for all newly created Outlook 2003 accounts is the cache mode of operation, thus improving the user’s experience and reducing the load placed on the Exchange servers. Messages are still available on the Exchange server, but they are cached locally for the user. You do, however, when creating the account to connect to the Exchange server, have the option to configure how Outlook is initially configured, as seen in Figure 7.17.
| Note |
|
![]() The configuration options available when using Outlook 2003 in cache mode are explained in Table 7.4.
The configuration options available when using Outlook 2003 in cache mode are explained in Table 7.4.
|
|
|
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
 Configuring RPC over HTTP
Configuring RPC over HTTP
![]() Another of the new features of Outlook 2003 when combined with Exchange Server 2003 is RPC over HTTP, which allows Outlook 2003 clients to connect securely to an Exchange Server 2003 organization over the Internet, which was previously impossible without the creation of a VPN tunnel before making the Outlook-to-Exchange connection. By configuring Outlook 2003 and Exchange Server 2003 to use RPC over HTTP, you allow users to connect to the Exchange organization over the Internet using Outlook instead of Outlook Web Access. As part of the configuration, you configure SSL for the HTTP connection to the front-end server. SSL is required because RPC over HTTP uses Basic authentication to authenticate users.
Another of the new features of Outlook 2003 when combined with Exchange Server 2003 is RPC over HTTP, which allows Outlook 2003 clients to connect securely to an Exchange Server 2003 organization over the Internet, which was previously impossible without the creation of a VPN tunnel before making the Outlook-to-Exchange connection. By configuring Outlook 2003 and Exchange Server 2003 to use RPC over HTTP, you allow users to connect to the Exchange organization over the Internet using Outlook instead of Outlook Web Access. As part of the configuration, you configure SSL for the HTTP connection to the front-end server. SSL is required because RPC over HTTP uses Basic authentication to authenticate users.
![]() Although RPC over HTTP is a powerful new feature, it is not without cost and burden. Unlike most configurations in Exchange Server 2003, configuring RPC over HTTP is not necessarily a simple process, because you will need to configure both the Exchange servers and the Outlook clients to make it work properly. In order to use RPC over HTTP, you must meet the following requirements:
Although RPC over HTTP is a powerful new feature, it is not without cost and burden. Unlike most configurations in Exchange Server 2003, configuring RPC over HTTP is not necessarily a simple process, because you will need to configure both the Exchange servers and the Outlook clients to make it work properly. In order to use RPC over HTTP, you must meet the following requirements:
-
 Client computers must have Outlook 2003 installed.
Client computers must have Outlook 2003 installed. -
 Client computers must be running Windows XP with Service Pack 1 and hot fix Q331320.
Client computers must be running Windows XP with Service Pack 1 and hot fix Q331320. -
 Front-end servers must be running Exchange Server 2003 on Windows Server 2003.
Front-end servers must be running Exchange Server 2003 on Windows Server 2003. -
 Back-end servers must be running Exchange Server 2003 on Windows Server 2003.
Back-end servers must be running Exchange Server 2003 on Windows Server 2003. -
 Public folder servers must be running Exchange Server 2003 on Windows Server 2003.
Public folder servers must be running Exchange Server 2003 on Windows Server 2003. -
 All Global Catalog servers must be running Windows Server 2003.
All Global Catalog servers must be running Windows Server 2003.
![]() If your network meets these stringent requirements and you have a need for RPC over HTTP, you can configure it by performing the following basic steps:
If your network meets these stringent requirements and you have a need for RPC over HTTP, you can configure it by performing the following basic steps:
-
 Configure the Exchange computer to use RPC over HTTP.
Configure the Exchange computer to use RPC over HTTP. -
 Configure the RPC virtual directory in Internet Information Services.
Configure the RPC virtual directory in Internet Information Services. -
 Configure the RPC proxy server to use specific ports.
Configure the RPC proxy server to use specific ports. -
 Configure the Outlook 2003 computer to use RPC over HTTP.
Configure the Outlook 2003 computer to use RPC over HTTP. -
 Verify that the connection can be made using RPC over HTTP.
Verify that the connection can be made using RPC over HTTP.Note  Users will likely ask why it is necessary to create an additional Outlook profile to use RPC over HTTP. This is done so that users can quickly choose between connection methods when starting up Outlook, depending on how they will be connecting to the Exchange organization. By configuring the profile ahead of time, you can prevent users from making the complicated configuration changes in Outlook and save some calls to the help desk.
Users will likely ask why it is necessary to create an additional Outlook profile to use RPC over HTTP. This is done so that users can quickly choose between connection methods when starting up Outlook, depending on how they will be connecting to the Exchange organization. By configuring the profile ahead of time, you can prevent users from making the complicated configuration changes in Outlook and save some calls to the help desk.Note  The process to configure and implement RPC over HTTP is not likely to be an exam item and is also very lengthy and complex. For these reasons it is not discussed in its entirety here. If you need the complete procedure to configure RPC over HTTP, be sure to see Knowledge Base article 833401, located at http://support.microsoft.com/default.aspx?scid=kb;en-us;833401.
The process to configure and implement RPC over HTTP is not likely to be an exam item and is also very lengthy and complex. For these reasons it is not discussed in its entirety here. If you need the complete procedure to configure RPC over HTTP, be sure to see Knowledge Base article 833401, located at http://support.microsoft.com/default.aspx?scid=kb;en-us;833401.
 The Office Custom Installation Wizard
The Office Custom Installation Wizard
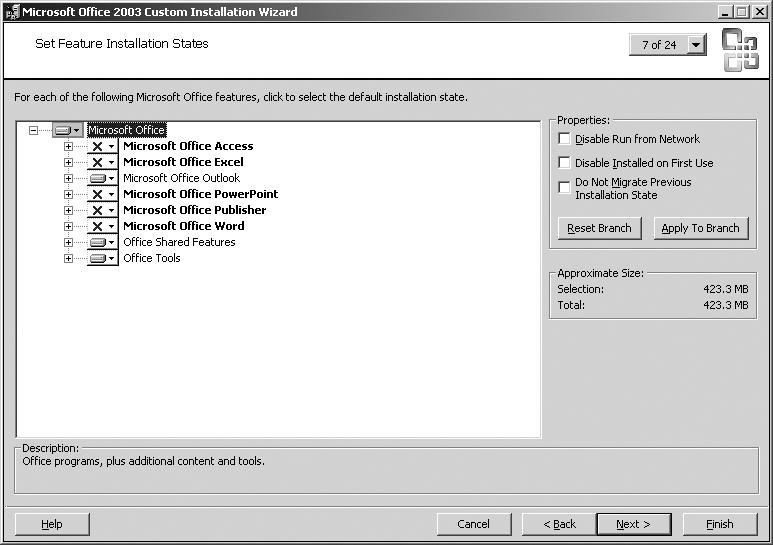
![]() As an administrator, you can customize the setup of Outlook in a few ways, including running the setup program with command-line options or using a settings file to answer various setup questions automatically instead of making the user answer them. However, the easiest and most powerful way to customize an installation of Outlook is with the Office Custom Installation Wizard, shown in Figure 7.18. This wizard is available as part of the Office 2003 Resource Kit, but it can also be freely downloaded from the Microsoft website as part of the Office 2003 Resource Kit Tools.
As an administrator, you can customize the setup of Outlook in a few ways, including running the setup program with command-line options or using a settings file to answer various setup questions automatically instead of making the user answer them. However, the easiest and most powerful way to customize an installation of Outlook is with the Office Custom Installation Wizard, shown in Figure 7.18. This wizard is available as part of the Office 2003 Resource Kit, but it can also be freely downloaded from the Microsoft website as part of the Office 2003 Resource Kit Tools.
![]() The Office Custom Installation Wizard works with Windows Installer to let you tweak almost every detail of the installation process. You can do the following:
The Office Custom Installation Wizard works with Windows Installer to let you tweak almost every detail of the installation process. You can do the following:
-
 Define the path where Outlook is installed on client computers.
Define the path where Outlook is installed on client computers. -
 Set the installation options (Run From Hard Drive, Install On First Use, Don’t Install) for individual features of Outlook 2003.
Set the installation options (Run From Hard Drive, Install On First Use, Don’t Install) for individual features of Outlook 2003. -
 Define a list of network servers for Windows Installer to use if the primary installation server is unavailable.
Define a list of network servers for Windows Installer to use if the primary installation server is unavailable. -
 Specify other products to install or other programs to run on the user’s computer when the Outlook installation is done.
Specify other products to install or other programs to run on the user’s computer when the Outlook installation is done. -
 Hide selected options from users during setup.
Hide selected options from users during setup. -
 Add custom files and Windows Registry settings to the installation.
Add custom files and Windows Registry settings to the installation. -
 Customize Desktop shortcuts for Outlook 2003.
Customize Desktop shortcuts for Outlook 2003. -
 Set user default options.
Set user default options. -
 Use Office Profile settings created with the Profile Wizard for Office 2003 to preset user options.
Use Office Profile settings created with the Profile Wizard for Office 2003 to preset user options.
![]() To accomplish all of this, the Windows Installer uses two types of files to install Outlook: an installer package (MSI) file and an installer transform (MST) file. The package contains a database that describes the configuration information. The transform file contains modifications that are to be made as Windows Installer installs Outlook. The package file never changes; it is essentially a database that helps Windows Installer relate various features to actual installation files. The transform file is what the Custom Installation Wizard helps you create. This means that you can create unique setup scenarios that all use the same installation files. In other words, you could create different installation routines for different departments but use only one network installation point for everyone to share.
To accomplish all of this, the Windows Installer uses two types of files to install Outlook: an installer package (MSI) file and an installer transform (MST) file. The package contains a database that describes the configuration information. The transform file contains modifications that are to be made as Windows Installer installs Outlook. The package file never changes; it is essentially a database that helps Windows Installer relate various features to actual installation files. The transform file is what the Custom Installation Wizard helps you create. This means that you can create unique setup scenarios that all use the same installation files. In other words, you could create different installation routines for different departments but use only one network installation point for everyone to share.
Virtual Servers in Exchange Server 2003
![]() As you learned in Chapter 2, “Microsoft Exchange Architecture,” Exchange Server 2003 relies heavily on Internet Information Services (IIS) to support access via Internet protocols. This integration with IIS also provides Exchange with the ability to configure virtual servers for Internet protocols. A virtual server enables you to host different protocols on the same physical server. The use of virtual servers provides added functionality and scalability. From the client perspective, there is no difference in connecting to a physical server or a virtual server. From the administrative perspective, virtual servers allow much greater flexibility and control than do individual physical servers that have to be created to support Internet protocols.
As you learned in Chapter 2, “Microsoft Exchange Architecture,” Exchange Server 2003 relies heavily on Internet Information Services (IIS) to support access via Internet protocols. This integration with IIS also provides Exchange with the ability to configure virtual servers for Internet protocols. A virtual server enables you to host different protocols on the same physical server. The use of virtual servers provides added functionality and scalability. From the client perspective, there is no difference in connecting to a physical server or a virtual server. From the administrative perspective, virtual servers allow much greater flexibility and control than do individual physical servers that have to be created to support Internet protocols.
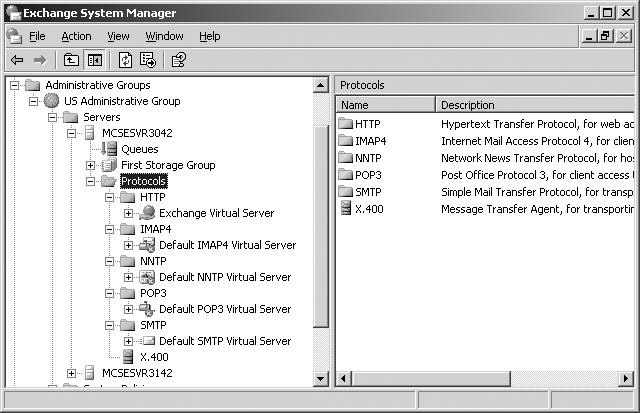
![]() When Exchange Server 2003 is installed, a virtual server is created by default for each Internet protocol, including SMTP, NNTP, HTTP, IMAP4, and POP3. Virtual servers are managed using the System Manager snap-in, as shown in Figure 7.19.
When Exchange Server 2003 is installed, a virtual server is created by default for each Internet protocol, including SMTP, NNTP, HTTP, IMAP4, and POP3. Virtual servers are managed using the System Manager snap-in, as shown in Figure 7.19.
![]() For the most part, the management of each type of virtual server is the same. You can right-click a virtual server and use the Pause, Stop, and Start commands to control the state of the service. Pausing a virtual server simply prevents new connections from being made to that server while the server itself remains running. Current connections are not disconnected. This is a graceful way of shutting down a virtual server that may be in use. When all users are finished, you can stop the server. Stopping the server will forcibly disconnect all connected users. If you want to disable certain protocols on a server-wide basis, stopping the virtual server for that protocol is usually the best way to go.
For the most part, the management of each type of virtual server is the same. You can right-click a virtual server and use the Pause, Stop, and Start commands to control the state of the service. Pausing a virtual server simply prevents new connections from being made to that server while the server itself remains running. Current connections are not disconnected. This is a graceful way of shutting down a virtual server that may be in use. When all users are finished, you can stop the server. Stopping the server will forcibly disconnect all connected users. If you want to disable certain protocols on a server-wide basis, stopping the virtual server for that protocol is usually the best way to go.
![]() Aside from these basic commands, you can also open property pages for each kind of virtual server. These pages are covered in the sections later in this chapter that deal with the individual protocols themselves.
Aside from these basic commands, you can also open property pages for each kind of virtual server. These pages are covered in the sections later in this chapter that deal with the individual protocols themselves.
| Note |
|
Microsoft Outlook Web Access
![]() Outlook Web Access (OWA) was first introduced to Exchange Server in version 5 and provides a way to access Exchange-based folders using a web browser such as Internet Explorer. OWA can be used to access e-mail, public folders, contact information, and calendar information. Since its introduction, OWA has become very popular, and its architecture has once again been completely overhauled with the introduction of Exchange Server 2003 Server. It has been redesigned to provide improved performance and a streamlined user interface.
Outlook Web Access (OWA) was first introduced to Exchange Server in version 5 and provides a way to access Exchange-based folders using a web browser such as Internet Explorer. OWA can be used to access e-mail, public folders, contact information, and calendar information. Since its introduction, OWA has become very popular, and its architecture has once again been completely overhauled with the introduction of Exchange Server 2003 Server. It has been redesigned to provide improved performance and a streamlined user interface.
![]() When using OWA, the only thing required on the client computers is Internet Explorer. This is also what makes OWA a good tool for cross-platform support, since versions of most web browsers exist for Windows, Macintosh, and Unix. In fact, OWA is the primary Exchange Server access method for users of Unix.
When using OWA, the only thing required on the client computers is Internet Explorer. This is also what makes OWA a good tool for cross-platform support, since versions of most web browsers exist for Windows, Macintosh, and Unix. In fact, OWA is the primary Exchange Server access method for users of Unix.
 OWA Features and Restraints
OWA Features and Restraints
![]() OWA is installed by default when you install Exchange Server 2003. Taking advantage of the ASP.NET service of Windows Server 2003, an OWA user can access many of the functions available through Outlook, including functionality for e-mail, calendar and group scheduling, public folders, and collaborative applications (when the forms have been developed with Microsoft Visual InterDev). Although OWA in Exchange Server 2003 is an almost perfect replacement for Outlook 2003, the following are some of the items that are not available when using OWA:
OWA is installed by default when you install Exchange Server 2003. Taking advantage of the ASP.NET service of Windows Server 2003, an OWA user can access many of the functions available through Outlook, including functionality for e-mail, calendar and group scheduling, public folders, and collaborative applications (when the forms have been developed with Microsoft Visual InterDev). Although OWA in Exchange Server 2003 is an almost perfect replacement for Outlook 2003, the following are some of the items that are not available when using OWA:
-
 Personal address books (because they are stored on your workstation)
Personal address books (because they are stored on your workstation) -
 Personal folders (PST files)
Personal folders (PST files) -
 WordMail and Microsoft Office integration
WordMail and Microsoft Office integration -
 Electronic forms creation
Electronic forms creation -
 Synchronizing local offline folders with server folders
Synchronizing local offline folders with server folders
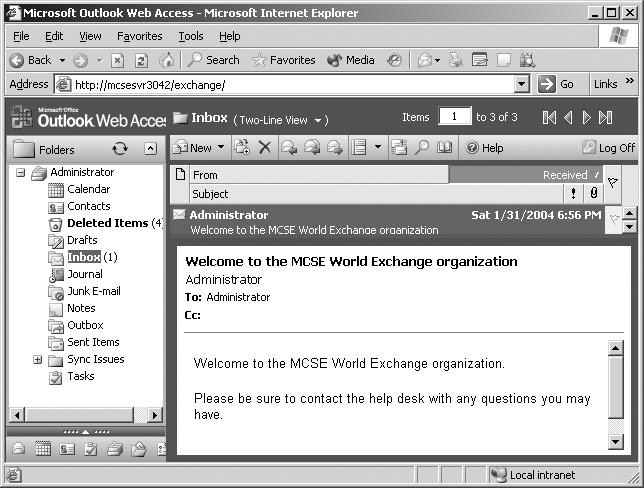
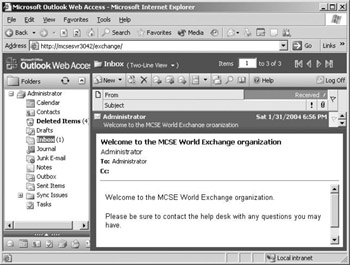
![]() Outlook Web Access simulates the look and feel of Outlook 2003, as shown in Figure 7.20. The ubiquity of the browser client makes OWA an attractive choice in environments that have a widespread mix of client platforms (such as Windows, Macintosh, and Unix) and that require shared client computers. Outlook Web Access is extremely useful for users who frequently move around among different workstations during the day and users who must access the Exchange server remotely via the Internet.
Outlook Web Access simulates the look and feel of Outlook 2003, as shown in Figure 7.20. The ubiquity of the browser client makes OWA an attractive choice in environments that have a widespread mix of client platforms (such as Windows, Macintosh, and Unix) and that require shared client computers. Outlook Web Access is extremely useful for users who frequently move around among different workstations during the day and users who must access the Exchange server remotely via the Internet.
 The OWA Process
The OWA Process
![]() The OWA process in Exchange Server 2003 is quite different from that of previous versions. OWA 5.x used Active Server Pages (ASP) to communicate with Exchange Server 5.5, which in turn used Collaboration Data Objects (CDO) 1.2 and MAPI. The effective number of users per server was limited by the overhead needed to support ASP and to run MAPI sessions within ASP. OWA was actually a part of IIS.
The OWA process in Exchange Server 2003 is quite different from that of previous versions. OWA 5.x used Active Server Pages (ASP) to communicate with Exchange Server 5.5, which in turn used Collaboration Data Objects (CDO) 1.2 and MAPI. The effective number of users per server was limited by the overhead needed to support ASP and to run MAPI sessions within ASP. OWA was actually a part of IIS.
![]() The new version of OWA does not use MAPI to communicate with the mailbox store and no longer uses ASP for client access. Instead, OWA is built into Exchange Server 2003’s new web store and uses IIS only to receive requests and pass them to the web store. Thus, IIS acts as an intermediary between the browser and OWA. IIS receives a client request, looks at the URL, and passes the appropriate information for the URL back to the web browser. If the server houses the Exchange Server 2003 database, OWA uses a high-speed channel to access the mailbox store. If the server is a front-end server, OWA redirects the request to a back-end server using HTTP.
The new version of OWA does not use MAPI to communicate with the mailbox store and no longer uses ASP for client access. Instead, OWA is built into Exchange Server 2003’s new web store and uses IIS only to receive requests and pass them to the web store. Thus, IIS acts as an intermediary between the browser and OWA. IIS receives a client request, looks at the URL, and passes the appropriate information for the URL back to the web browser. If the server houses the Exchange Server 2003 database, OWA uses a high-speed channel to access the mailbox store. If the server is a front-end server, OWA redirects the request to a back-end server using HTTP.
![]() OWA is actually not a client itself but rather a set of Active Server Pages that run in the context of Microsoft’s IIS. Client web browsers access IIS using HTTP over TCP port 80, by default, and in turn IIS accesses the OWA component on behalf of the clients using an extended version of HTTP known as HTTP-DAV. HTTP-DAV adds several features to HTTP such as file locking, namespace management, and document property access.
OWA is actually not a client itself but rather a set of Active Server Pages that run in the context of Microsoft’s IIS. Client web browsers access IIS using HTTP over TCP port 80, by default, and in turn IIS accesses the OWA component on behalf of the clients using an extended version of HTTP known as HTTP-DAV. HTTP-DAV adds several features to HTTP such as file locking, namespace management, and document property access.
![]() Many components play an important role in the OWA process, including the following:
Many components play an important role in the OWA process, including the following:
-
 Active Directory
Active Directory -
 Information Store
Information Store -
 The Exchange DSAccess component, which enables Exchange Server 2003 components to communicate with Active Directory (DSAccess uses the LDAP protocol to perform this communication)
The Exchange DSAccess component, which enables Exchange Server 2003 components to communicate with Active Directory (DSAccess uses the LDAP protocol to perform this communication) -
 OLE DB Provider for Exchange (ExOLEDB), which acts as the interface between DAVEx and EXIPC (both discussed a bit later)
OLE DB Provider for Exchange (ExOLEDB), which acts as the interface between DAVEx and EXIPC (both discussed a bit later) -
 Directory Service to the IIS metabase (DS2MB), which provides a one-way synchronization of configuration information from Active Directory to the IIS metabase
Directory Service to the IIS metabase (DS2MB), which provides a one-way synchronization of configuration information from Active Directory to the IIS metabase -
 EXIPC, a queuing engine that is used to pass information between the IIS and Information Store components
EXIPC, a queuing engine that is used to pass information between the IIS and Information Store components -
 IIS metabase, which is a Registry database for IIS configuration
IIS metabase, which is a Registry database for IIS configuration -
 W3svc, the World Wide Web publishing service of IIS
W3svc, the World Wide Web publishing service of IIS -
 DAVEx, a component that passes client requests between W3svc and the Information Store
DAVEx, a component that passes client requests between W3svc and the Information Store -
 ExProx, which acts as a protocol proxy on a front-end server if a front-end/back-end server configuration is being used
ExProx, which acts as a protocol proxy on a front-end server if a front-end/back-end server configuration is being used -
 Forms Registry, which stores the OWA forms rendered by IIS and passed to the client
Forms Registry, which stores the OWA forms rendered by IIS and passed to the client
![]() As you can see, the OWA process is fairly complicated and involves a number of components. The complexity of the process is basically designed to ensure that each major tool in use does what it is good at and that the client needs no special configuration. Since the client needs to be able to access Exchange using a standard web browser, its only responsibility must be to request a simple URL, such as http://owa.microsoft.com/exchange, from a web server (in this case IIS) and display the results in its window. Everything else must happen on the server end. For example, to open a user’s contacts, type the path to the user’s mailbox followed by /contacts, as in http://owa.microsoft.com/exchange/user/contacts, where user is the user’s mailbox name.
As you can see, the OWA process is fairly complicated and involves a number of components. The complexity of the process is basically designed to ensure that each major tool in use does what it is good at and that the client needs no special configuration. Since the client needs to be able to access Exchange using a standard web browser, its only responsibility must be to request a simple URL, such as http://owa.microsoft.com/exchange, from a web server (in this case IIS) and display the results in its window. Everything else must happen on the server end. For example, to open a user’s contacts, type the path to the user’s mailbox followed by /contacts, as in http://owa.microsoft.com/exchange/user/contacts, where user is the user’s mailbox name.
![]() Here is the actual process that occurs when a client’s browser requests information from an Exchange server:
Here is the actual process that occurs when a client’s browser requests information from an Exchange server:
-
 W3svc in IIS receives the request and authenticates the user by querying Active Directory.
W3svc in IIS receives the request and authenticates the user by querying Active Directory. -
 Once authentication is complete, W3svc relays the request to the DAVEx component.
Once authentication is complete, W3svc relays the request to the DAVEx component. -
 DAVEx transfers the request through the EXIPC queue to the Information Store.
DAVEx transfers the request through the EXIPC queue to the Information Store. -
 The Information Store retrieves the appropriate data and returns it to DAVEx.
The Information Store retrieves the appropriate data and returns it to DAVEx. -
 DAVEx retrieves an appropriate form from the Forms Registry and merges it with the information from the Information Store, creating an HTML or XML document.
DAVEx retrieves an appropriate form from the Forms Registry and merges it with the information from the Information Store, creating an HTML or XML document. -
 DAVEx sends the formatted document back to W3svc.
DAVEx sends the formatted document back to W3svc. -
 W3svc sends the information back the client, which displays it in the browser window.
W3svc sends the information back the client, which displays it in the browser window.
 Installing and Configuring OWA
Installing and Configuring OWA
![]() OWA is installed as part of the default setup of Exchange Server 2003, and it is configured by default to allow access to users’ mailboxes and the default public folder tree. However, you can configure the server to provide customized access for clients by specifying which users can access the server, which authentication method(s) to allow, and which public folders are exposed to users.
OWA is installed as part of the default setup of Exchange Server 2003, and it is configured by default to allow access to users’ mailboxes and the default public folder tree. However, you can configure the server to provide customized access for clients by specifying which users can access the server, which authentication method(s) to allow, and which public folders are exposed to users.
![]() Since Outlook Web Access begins running when Exchange Server is installed, no special setup options are required other than a standard Exchange installation. The OWA client can offer your users much of the functionality offered by using Outlook 2003 from remote locations. Using a dedicated server for OWA can also increase network security by exposing only this dedicated server to the Internet.
Since Outlook Web Access begins running when Exchange Server is installed, no special setup options are required other than a standard Exchange installation. The OWA client can offer your users much of the functionality offered by using Outlook 2003 from remote locations. Using a dedicated server for OWA can also increase network security by exposing only this dedicated server to the Internet.
![]() When you install Exchange Server 2003, web access is installed and configured by default, and an Exchange virtual root and a Public virtual root are added to the IIS directory tree. These virtual roots point to their corresponding directories in Exchange Server 2003—the directories that hold the public store and the mailbox store.
When you install Exchange Server 2003, web access is installed and configured by default, and an Exchange virtual root and a Public virtual root are added to the IIS directory tree. These virtual roots point to their corresponding directories in Exchange Server 2003—the directories that hold the public store and the mailbox store.
![]() To access mail folders from within the corporate intranet, users will need to enter the following address in their web browser: http://servername/exchange/user/, where servername is the name of the Exchange server, exchange is the default private web folder, and userid is the alias of the user. For connecting via the Internet, the above URL must be appended by the Fully Qualified Domain Name of the domain on which Exchange is running, for example, http://servername.domain.com/exchange/user/.
To access mail folders from within the corporate intranet, users will need to enter the following address in their web browser: http://servername/exchange/user/, where servername is the name of the Exchange server, exchange is the default private web folder, and userid is the alias of the user. For connecting via the Internet, the above URL must be appended by the Fully Qualified Domain Name of the domain on which Exchange is running, for example, http://servername.domain.com/exchange/user/.
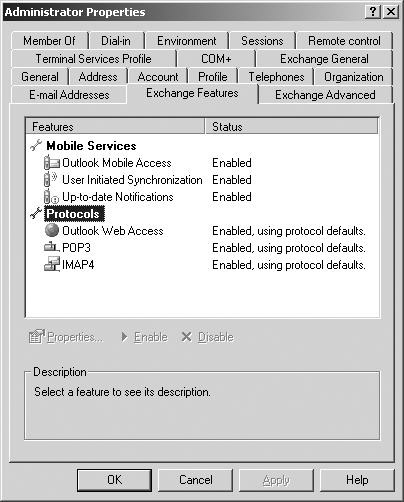
![]() Web access to Exchange Server 2003 is enabled for all users by default. To change this configuration, use Active Directory Users and Computers. On the Exchange Features tab of the user Properties dialog box, seen in Figure 7.21, you can enable or disable HTTP, IMAP4, and POP3 access to the Exchange organization.
Web access to Exchange Server 2003 is enabled for all users by default. To change this configuration, use Active Directory Users and Computers. On the Exchange Features tab of the user Properties dialog box, seen in Figure 7.21, you can enable or disable HTTP, IMAP4, and POP3 access to the Exchange organization.
 User Authentication in OWA
User Authentication in OWA
![]() Users of OWA must be authenticated in some form before anything but Anonymous access is granted. A number of options are available for OWA authentication. Choosing the appropriate mechanism is usually a matter of the capabilities of the client operating system and specific security policies. In a single-server environment, the default authentication method for OWA is Anonymous authentication and Integrated Windows authentication (similar to NTLM). In a multi-server environment, the default authentication is Basic (clear-text) and NTLM. Authentication is set via the HTTP virtual servers configured for OWA. This configuration is actually set in Internet Information Server. Microsoft recommends configuring authentication on the back-end Exchange server only. The default authentication settings are the same on the front-end Exchange server, but securing the back-end server is much more important. In addition, authentication conflicts between the front end and back end could jeopardize user access. Exercise 7.1 outlines the steps for configuring OWA authentication. But first we must define the available types of authentication.
Users of OWA must be authenticated in some form before anything but Anonymous access is granted. A number of options are available for OWA authentication. Choosing the appropriate mechanism is usually a matter of the capabilities of the client operating system and specific security policies. In a single-server environment, the default authentication method for OWA is Anonymous authentication and Integrated Windows authentication (similar to NTLM). In a multi-server environment, the default authentication is Basic (clear-text) and NTLM. Authentication is set via the HTTP virtual servers configured for OWA. This configuration is actually set in Internet Information Server. Microsoft recommends configuring authentication on the back-end Exchange server only. The default authentication settings are the same on the front-end Exchange server, but securing the back-end server is much more important. In addition, authentication conflicts between the front end and back end could jeopardize user access. Exercise 7.1 outlines the steps for configuring OWA authentication. But first we must define the available types of authentication.
![]() Basic authentication Basic authentication, also referred to as plain-text or clear-text, is commonly used on intranets. Unlike the NTLM protocol, which accepts established users’ identification through the access token, Basic authentication relies on users to enter their username, domain, and password. Basic authentication is independent of the browser, which also makes it independent of the platform being used. Basic authentication results in the transmission of unencrypted passwords over the network, which makes it a relatively insecure method of authentication. Users must enter their username, domain, and password each time they log on.
Basic authentication Basic authentication, also referred to as plain-text or clear-text, is commonly used on intranets. Unlike the NTLM protocol, which accepts established users’ identification through the access token, Basic authentication relies on users to enter their username, domain, and password. Basic authentication is independent of the browser, which also makes it independent of the platform being used. Basic authentication results in the transmission of unencrypted passwords over the network, which makes it a relatively insecure method of authentication. Users must enter their username, domain, and password each time they log on.
![]() Integrated Windows authentication Integrated Windows authentication works differently depending upon the situation. The optimal authentication takes place when the client is running Windows 2000 (or later) and Internet Explorer 5 (or later), in which case Kerberos provides the best security available. With other pre–Windows 2000 clients, Integrated Windows authentication uses the NTLM protocol instead of Kerberos. Integrated Windows authentication always encrypts the client’s password, which provides excellent security. It also allows browser access without prompting the users for their user ID and password. Integrated Windows authentication does not work with browsers other than Internet Explorer 4 and 5, and it is not available in a front-end and back-end Exchange Server configuration.
Integrated Windows authentication Integrated Windows authentication works differently depending upon the situation. The optimal authentication takes place when the client is running Windows 2000 (or later) and Internet Explorer 5 (or later), in which case Kerberos provides the best security available. With other pre–Windows 2000 clients, Integrated Windows authentication uses the NTLM protocol instead of Kerberos. Integrated Windows authentication always encrypts the client’s password, which provides excellent security. It also allows browser access without prompting the users for their user ID and password. Integrated Windows authentication does not work with browsers other than Internet Explorer 4 and 5, and it is not available in a front-end and back-end Exchange Server configuration.
![]() Anonymous authentication Anonymous authentication, which IIS also allows, provides limited access to specific public folders and directory information. All browsers support Anonymous authentication, making it an easy way to provide insecure access to public folder data. A single point of configuration makes administration simple. Anonymous authentication does not identify users uniquely. Consequently, you cannot track usage by user.
Anonymous authentication Anonymous authentication, which IIS also allows, provides limited access to specific public folders and directory information. All browsers support Anonymous authentication, making it an easy way to provide insecure access to public folder data. A single point of configuration makes administration simple. Anonymous authentication does not identify users uniquely. Consequently, you cannot track usage by user.
![]() Secure Sockets Layer authentication Secure Sockets Layer (SSL) provides the best level of security because the entire communications session is encrypted. SSL is not an authentication mechanism itself. Rather, SSL provides a secure channel for other authentication mechanisms. Although any authentication mechanism can be used with SSL, the most common implementation with SSL is Basic (clear-text). Most browsers support SSL communication. SSL creates a substantial amount of overhead in providing this security, so SSL communications tend to reduce the overall performance of an authenticating server and generate increased network traffic.
Secure Sockets Layer authentication Secure Sockets Layer (SSL) provides the best level of security because the entire communications session is encrypted. SSL is not an authentication mechanism itself. Rather, SSL provides a secure channel for other authentication mechanisms. Although any authentication mechanism can be used with SSL, the most common implementation with SSL is Basic (clear-text). Most browsers support SSL communication. SSL creates a substantial amount of overhead in providing this security, so SSL communications tend to reduce the overall performance of an authenticating server and generate increased network traffic.
![]() All in all, Outlook Web Access is a powerful means of providing cross-platform and remote access to your Exchange server. Authenticated users can log on to their personal accounts to access e-mail, public folders, and collaborative tools. Using web-based public folder access, an organization could even build private and public discussion forums on the Internet or on private intranets.
All in all, Outlook Web Access is a powerful means of providing cross-platform and remote access to your Exchange server. Authenticated users can log on to their personal accounts to access e-mail, public folders, and collaborative tools. Using web-based public folder access, an organization could even build private and public discussion forums on the Internet or on private intranets.
-
 Click Start > Programs > Administrative Tools > Internet Information Services (IIS) Manager.
Click Start > Programs > Administrative Tools > Internet Information Services (IIS) Manager. -
 Expand the container for the server running OWA.
Expand the container for the server running OWA. -
 Expand the default website container.
Expand the default website container. -
 Right-click the Exchweb object and select Properties from the shortcut menu.
Right-click the Exchweb object and select Properties from the shortcut menu. -
 Click the Directory Security tab.
Click the Directory Security tab. -
 Click the Edit button in the Authentication And Access Control section at the top of the page.
Click the Edit button in the Authentication And Access Control section at the top of the page. -
 Select the forms of access that you want to allow.
Select the forms of access that you want to allow. -
 Click OK twice to return to Internet Information Services (IIS) Manager.
Click OK twice to return to Internet Information Services (IIS) Manager.

0 comments
Post a Comment