Introduction
The ISA firewall can act in a number of roles: as a front-end edge firewall that sits in front of the entire company, as a back-end firewall located behind another edge firewall that might be an ISA firewall or another type of firewall, or as a perimeter network firewall that walls off critical network servers and services from the rest of the network. We’ll focus on the third configuration in this chapter.
In spite of eye-catching headlines about the death of the DMZ and the imminent demise of network security zones, the fact is that we who live in the trenches still need to live with the current reality, where network perimeters need to be defined to provide access controls on hosts connecting to other hosts belonging to different security zones. And although Network Access Protection (NAP; expected to be implemented in Longhorn/Vista) and IPSec-based domain isolation hold a lot of promise, there are and will be significant technological hurdles that have to be jumped before those methodologies will be applicable for widespread use.
Instead of proclaiming the death of the DMZ, security experts should be making the clarion call for increased perimeterization.You’ll go a long way toward improving your network’s security position by grouping hosts into different security zones, and putting firewalls and other network security devices between those zones that enable strong access controls on communications between those zones.
In this chapter, we’ll examine the requirements and procedures involved with creating a network services segment separated from the rest of the corporate network by an ISA firewall.You can put an ISA firewall in front of the network services located on the services segment to help protect those critical network services from being adversely affected by outbreaks that take place on other network segments.
The key concept here is that only required communications are allowed to and from the network services segment; all other communications are blocked. In addition to limiting communications only to the hosts and protocols that are required for access, we will leverage the ISA firewall’s advanced stateful packet and application layer inspection mechanisms to help secure the communications allowed to the network services segment.
Network Services Segment Configuration Options
As with all network security devices, and especially for network firewalls, there is no such thing as “one size fits all” when it comes to configuration.There is no replacement for understanding how your firewall works, and how to configure it to meet your organization’s specific requirements.
We should look at two scenarios before proceeding with a step-by-step example for configuring a network services segment behind an ISA firewall.These scenarios are:
-
Scenario 1 A local area network (LAN) router separates the edge ISA firewall from the rest of the corporate network.
-
Scenario 2 No LAN router separates the edge ISA firewall from the rest of the corporate network.
Although there are variations on the second theme, our discussions of these two scenarios will hopefully make clear what your configuration options are when you do and don’t have a LAN router on your network.
Scenario 1: A LAN Router between the ISA Firewall and Corporate Network
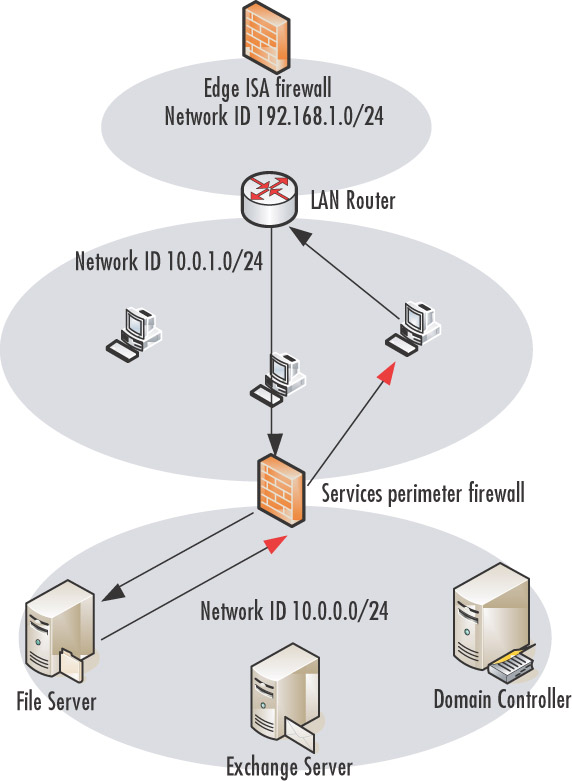
high-level view of scenario 1 appears in Figure 10.1. In this scenario, there is a LAN router between the edge ISA firewall and the rest of the network.There also is a Route relationship between all internal networks located behind the edge ISA firewall. Network address translation (NAT) is used only for communications to the Internet.
In this scenario, hosts on the corporate network in front of the network services perimeter ISA firewall use a default gateway that is the local address of the LAN router.The LAN router is configured with a route of last resort (which allows it to access the Internet) that is the internal address on the edge ISA firewall.The LAN router is configured with a routing table entry that provides a route to the network ID located behind the network services perimeter network ISA firewall.
When a user makes a request to a server on the network services segment located behind the network services perimeter ISA firewall, the request is forwarded to the client’s default gateway address, because the connection is to a nonlocal (remote) network.The packet is forwarded based on the routing table entry on the LAN router to the Internet Protocol (IP) address on the external interface of the network services perimeter ISA fire-wall, and then the network services perimeter ISA firewall routes the request to the server on the network services segment.
The black arrows in Figure 10.1 show the request path, and the red arrows show the response path.The server on the services segment sends the response to its default gateway, which is the IP address on the internal interface of the network services segment perimeter ISA firewall.The response is forwarded directly to the client making the request because the ISA firewall has knowledge of all network IDs to which it is directly connected.The response is not forwarded to the LAN router and then back to the client. Note that the request and response paths are not the same.
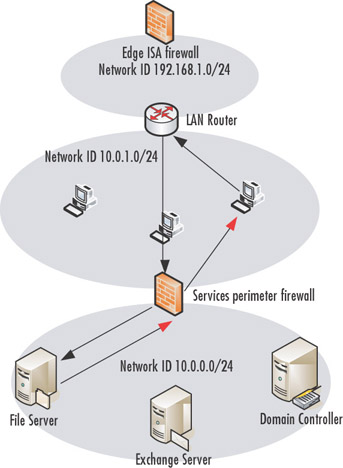
Figure 10.2 shows the request and response paths for connections made to the Internet. Notice in this case that the request and response paths are the same.
Scenario 2: No LAN Router between the ISA Firewall and Corporate Network
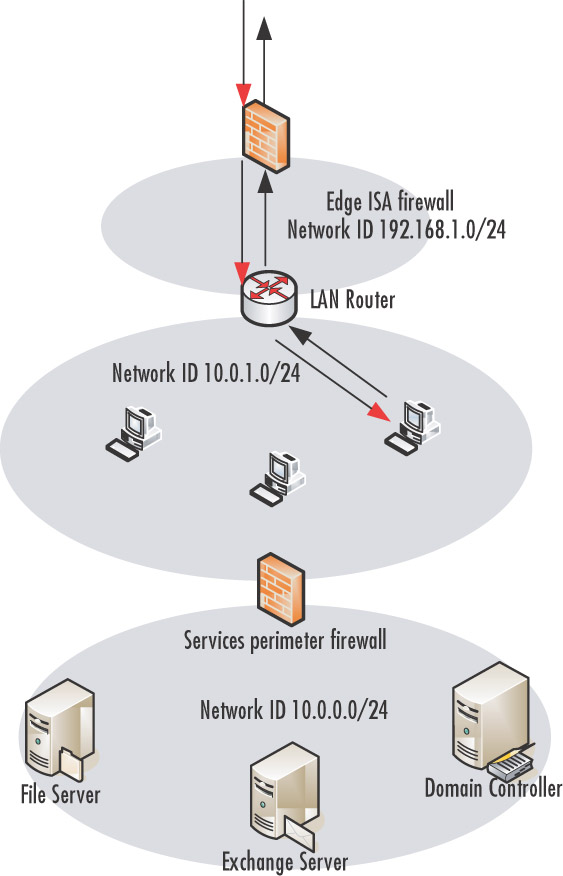
Now let’s look at scenario 2, where there is no router between the ISA firewall and the rest of the network (see Figure 10.3). In this case, the clients on the corporate network use the internal interface of the edge ISA firewall as their default gateway address.The edge ISA fire-wall is configured with a routing table entry informing the edge ISA firewall of the correct route to network ID 10.0.0.0/24.The ISA firewall forwards the connection to the IP address on the external interface of the network services perimeter ISA firewall, which then routes the connection to the server on the network services segment.
The response from the server on the network services segment is forwarded to the server’s default gateway address, which is the IP address on the internal interface of the network services perimeter ISA firewall, which in turn forwards the response directly to the client machine that made the request. Notice that the request and response paths are not the same.This scenario works because the ISA firewall handling traffic has knowledge of and is not dealing with response traffic to connections it is not aware of.This will be made clear in the next figure.



0 comments
Post a Comment